The Biggest, Longest Hack
How the American taxpayer foots the bill for the Chinese Communist Party to work hand-in-glove with the U.S. Intelligence Community to spy on the world...and blame each other all the way to the bank.
***updated April 13, 2024 at 19:39 to provide more detail on Microsemi’s talent pool and to expand with more sources on the continuing ability of Supermicro to get its products with banned chips to China***
***updated April 14, 2024 at 17:19 to expand detail on Fortinet’s research with the Seven Sons of National Defence school, Beijing Institute of Technology***
What this report hopes to present is an overwhelming, indisputable volume of evidence of a practice that does at its core strike as a counter to two primary principles that We hold are fundamental to what the Founders enshrined in the United States Constitution 250 years ago: personal sovereignty and national security.
Supermicro
For well over a decade, one particular American computer server manufacturer, Super Micro Computer, Inc. (NASDAQ: SMCI, known commonly as “Supermicro”), has been accused of serious security vulnerabilities built into their products.
As far back as 2013, InfoWorld was reporting that Supermicro’s motherboards and their firmware — the hard-coded software into the tiny little chips on each silicon board — were “far from secure.”1
In 2014, CARI.net reported a bug that continually exposed administrator passwords to the server even despite firmware updates by connecting to port 49152.2 ARS Technica’s write-up on the report was fairly definitive and corroborated the CARI findings.3
But then in 2018, a bombshell Bloomberg Businessweek report titled The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies dropped a motherlode of backstory on a CIA-funded company called Elemental Technologies, Amazon, Supermicro, and a shadowy, hush-hush federal investigation.4
But more importantly, the story revolved around very mysterious details that many critics disputed as outlandish or completely false at the time and ever since.
“Three senior insiders at Apple say that in the summer of 2015, it, too, found malicious chips on Supermicro motherboards. Apple severed ties with Supermicro the following year, for what it described as unrelated reasons.”
-Bloomberg Businessweek: “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies”
Tim Cook demanded a retraction of the story in the aftermath, and Apple, Supermicro, Amazon, the Chinese Government, and federal agencies and departments involved all denied any knowledge of the occurrence outright.5 Oddly counterintuitive to Cook’s protest however, Apple had already cut ties with the motherboard maker months prior in 2017 citing a “security concern.”6
Supermicro released several subsequent investor and press statements in response to the Bloomberg Businessweek exposé and released customer letters to update interested parties to the company’s self-auditing process on only a sampling of their products.7
“...A representative sample of our motherboards was tested, including the specific type of motherboard depicted in the article and motherboards purchased by companies referenced in the article, as well as more recently manufactured motherboards...”
-Super Micro Computer, Inc.
Just weeks before the Jordan Robertson and Michael Riley piece for Bloomberg Businessweek, Security Affairs had published an article declaring that a critical flaw in Supermicro’s server update process allowed persistent malware;8 hearkening back to the prior, repeated vulnerabilities and outright threats that the computer servers reportedly posed.9
Deep within the sprawling article was the meat and potatoes: a description of the “illicit chips” buried within the baseboard management controller, or “BMC,” which effectually opened the computer’s system to any sort of modifications that a system administrator could perform — anything down to rewriting code underlying the entire operating system.
“Since the implants were small, the amount of code they contained was small as well. But they were capable of doing two very important things: telling the device to communicate with one of several anonymous computers elsewhere on the internet that were loaded with more complex code; and preparing the device’s operating system to accept this new code. The illicit chips could do all this because they were connected to the baseboard management controller, a kind of superchip that administrators use to remotely log in to problematic servers, giving them access to the most sensitive code even on machines that have crashed or are turned off.
This system could let the attackers alter how the device functioned, line by line, however they wanted, leaving no one the wiser. To understand the power that would give them, take this hypothetical example: Somewhere in the Linux operating system, which runs in many servers, is code that authorizes a user by verifying a typed password against a stored encrypted one. An implanted chip can alter part of that code so the server won’t check for a password—and presto! A secure machine is open to any and all users. A chip can also steal encryption keys for secure communications, block security updates that would neutralize the attack, and open up new pathways to the internet.”
Possibly more alarming yet within the Bloomberg Businessweek article was the outrageous-sounding claim that these servers and systems could update even when turned off.
Fact-checking Bloomberg Businessweek
Servethehome.com reported as a 5-page fact check with extensive background knowledge an analysis of the Bloomberg BW 2018 article that the bombshell story didn’t add up to how the technology actually operates, as it was told.10
This extensive fact-check with the original source of the statements cited in the Bloomberg BW article points to something of a more widespread pandemic of vulnerabilities baked into federal and, more importantly, military cyber infrastructures (of every first-world nation).
According to the taxpayer-funded watchdog site, “USASpending.gov,” the keyword search for “Supermicro” returned around $15 million in government contracts in some form through the end of 2018. Most of that $15 million — $11.8 million, according to USASpending.gov to be exact — was to the U.S. Department of Defense.
The original source of the Bloomberg BW article, Yossi Appleboum, indicated that nearly all network equipment at-large was more widely affected by this kind of malware/nefarious programming effort than simply only Supermicro.
“I want to be quoted. I am angry and I am nervous and I hate what happened to the story.
Everyone misses the main issue.”
-Yossi Appleboum on the fallout of Bloomberg Businessweek’s “The Big Hack”
Not long after the October 2018 article, in February of 2019, Supermicro announced in a press release: “Supermicro Brings AI Inferencing to the Edge to Process Large Data Volumes Demanded by 5G Workloads while enabling High Speed Streaming and Low Latency User Experiences.”11
In November of the same year, Supermicro released a horde of firmware updates with a new security feature — a “Unique Password Security Feature” — for ALL of its prior products. Up until then, Supermicro used a pre-loaded “ADMIN” password, pre-loaded standard on every product, all spelled out in black and white in the Supermicro press release.12
“The Long Hack”
The hits didn’t stop for Supermicro following the 2018 Bloomberg Businessweek earthquake of an article, either. Bloomberg followed up the October 2018 story with another hit in 2021, just after the January 6th Capitol riots that were spawned largely by accusations of insecure voting systems.
The follow-up 2021 Bloomberg exposé, “The Long Hack,” claimed that:
“U.S. spymasters discovered the manipulations but kept them largely secret as they tried to counter each one and learn more about China’s capabilities.”
-”The Long Hack,” Jordan Robertson and Michael Riley, Bloomberg - 12 Feb 2021
The article continued to recount the timeline, also laid out in the prior 2018 article. In Bloomberg’s retracing the events around the Supermicro saga, the writers baked in the U.S. Intelligence Community’s hard line narrative of China’s implicit guilt in the matter.13
“China’s exploitation of products made by Supermicro, as the U.S. company is known, has been under federal scrutiny for much of the past decade, according to 14 former law enforcement and intelligence officials familiar with the matter. That included an FBI counterintelligence investigation that began around 2012, when agents started monitoring the communications of a small group of Supermicro workers, using warrants obtained under the Foreign Intelligence Surveillance Act, or FISA, according to five of the officials.”
But later in the 2021 article, Bloomberg’s writers made it clear that the federal government were counterintuitively doing everything within reason to keep any supposed ongoing investigations entirely under wraps, even to Supermicro themselves.
“Supermicro itself wasn’t told about the FBI’s counterintelligence investigation, according to three former U.S. officials…
…‘This is real,’ Janke said, ‘and the government knows it.’”
There were continuing problems for Supermicro, however.
The tech research group Binarly reported in October of 2023 of major vulnerabilities in Supermicro’s Intelligent Platform Management Interface, or IPMI.14

The report echoed the same kind of firmware issues that follow a very familiar pattern. For those who have taken issue with the Five Eyes intelligence alliance (U.S., Australia, Canada, New Zealand, U.K.) and the unconstitutional snooping on American citizens and businesses by the U.S. government uncovered by WikiLeaks and the former NSA contractor now in Russian exile, Edward Snowden, this information likely comes as no surprise.
Most recently, DOJ placed the computer giant Supermicro under investigation for abnormal accounting practices.15
Smells Like I.C. Spirit
The Intercept chimes in (2019)
Micah Lee and Henrik Moltke reminded The Intercept’s audience in 2019 that Edward Snowden’s leaks of classified NSA materials exposed extensive ability and practice of the U.S. Intelligence Community infiltrating Chinese supply chains and some of the tools they use carry out these precise kinds of attacks, themselves.16
“The documents also detail how the U.S. and its allies have themselves systematically targeted and subverted tech supply chains, with the NSA conducting its own such operations, including in China, in partnership with the CIA and other intelligence agencies.”
The premise of the January 2019 report transparently pointed out the irrelevance of Bloomberg’s reporting to the basis of The Intercept’s wider focus.
The story’s stark implications severely blur the lines between the Pentagon, U.S. Intelligence Community, China Ministry of State Security, and the People’s Liberation Army after taking into account the contents of this report.
This occurred despite endless bi-partisan accusations of tampering around the 2016, 2020, and 2024 elections through hacking and other known cybersecurity vulnerabilities.
The Equation Group template
In 2015, the cybersecurity firm Kaspersky released materials outlining revelations of what most experts link to the NSA spying program.1718 Kaspersky was banned from operating within the United States by the Biden Administration in 2024.19
Dan Goodin at ARS Technica penned an article in 2015 that declared what was “hid for 14 years,” dating the allegations of the NSA’s clandestine activity to 2001.20 In the article, Goodin borrowed a graphic from the Kaspersky research that showed the United States even with infections by the alleged NSA-linked group, as the report21 also highlighted.
Notice in the Kaspersky “victims map” that the United States was also listed as a “victim,” though to a lesser degree than the presumptive American adversaries.
If true, and if Equation Group is indeed an NSA hacking toolkit, this would be severely unconstitutional.
In April of 2001, the Davos World Economic Forum was hacked using a “worm attack,” usually another term for “self-executing malware,” attack along the same lines of malware attack vectors,22 followed by the Code Red attack just before 9/11,23 followed again by the Nimda Worm that was announced exactly one week after 9/11.2425
In early March of 2015, Trevor Timm at The Guardian penned a column over the Obama White House wanting “tech companies to hand over encryption keys or build backdoors” while simultaneously blasting China for their alleged hacks into American infrastructure.26
Timm’s simple, but realistically viable premise built around Snowden’s revelations and the NSA’s stealing of encryption keys open the door to questioning whether the “good guys” could be working with the “bad guys,” or whether there is even any separation between them at all.
Common Denominators
Collectively, this all most likely points to a much smaller, more prevalent and common component quite literally “baked” into countless motherboards and even inside other chips — a component called a “Field-Programmable Gate Array,” or FPGA.
These tiny, wildly common components would be a prime target of a firmware update containing tiny, undetectable snippets of malware to be reassembled by a separate code to trigger the malware at a later time.
An FPGA can serve as an incredibly efficient flash memory storage medium and utilizes very low amounts of power. This combination of agility and efficiency make it a key component to network monitoring and “debugging” networks, and as an enabling component within systems-on-a-chip (SOC) and Application-Specific Integrated Circuits (ASIC).
“Debugging” is often performed through remote access of the BMCs as an industry-standard feature, which means constant packet* loss monitoring, and constant data analysis, internally, but oftentimes, this process is also performed remotely by running a parallel, simultaneous stream of data from the device to a third location.
*”Packets” are individual units of data that constitute whole data transmissions. FPGAs can also help in the repair of “packet loss” that can occur whilst transmitting data across a medium, a standard and necessary integration for cloud computing.
Major cybersecurity quagmire
In 2012, a Russian researcher at Cambridge University named Sergei Skorobogatov along with Christopher Woods at Quo Vadis Labs in London published a research paper titled, “Breakthrough silicon scanning discovers backdoor in military chip,” which alleged a first real world detection of a backdoor in a military grade FPGA.27
The FPGA model that the researchers tested using their “innovative patented technique” was the Actel/Microsemi ProASIC3, a supposedly military-grade “secure” ASIC that was designed to withstand and perform under high levels of radiation and extreme hot and cold temperatures, making the ProASIC series a go-to micro-component for aerospace industry customers.
According to the research, the study found definitively, that the back doors were “deliberate, ” and were also found in all of Actel/Microsemi’s other lines of FPGAs.
The study specifically mentioned that if the security key were known, commands could be maliciously embedded and to attack remotely using a “Stuxnet-type attack via a network or the Internet on the silicon itself.”
Even detractors of the story were forced to admit the existence of the backdoor while downplaying the severity or the source of the vulnerability.28
The Microsemi ProASIC3, according to the Cambridge University research, is a military-grade FPGA, indicating a widespread use of FPGAs in or as ASIC systems. The sidechaining, or “parallel computing,” possibilities are thereby endless.
In totality, the likelihood of the Equation Group being linked to the United States National Security Agency while their having knowledge and subsequent disregard for “backdoors” makes it important to consider the “How?” of covert firmware manipulation at the research and development level.
Phoenix Rising
Continuing on with the Cambridge research into the Actel/Microsemi ProASIC3, Microsemi was a leading chipmaker specializing in military-grade FPGA chips based in Irvine/Aliso Viejo, California, and was acquired by Chandler, Arizona chip manufacturing giant Microchip in 2018 for $10.3 billion.29
Arizona State University rightly advertises the Greater Phoenix area as “ground zero” for semiconductors.30 Microchip has been an industry partner with Arizona State University through their Polytechnic campus in nearby Mesa, Arizona since at least 2008.31
In 2019, Microsemi supported Arizona State University’s Meteor Studio alongside Samsung, NVIDIA, and Xilinx.32
According to ASU’s Meteor Studio’s landing page, the lab works with “advanced visual capture and processing systems,” “systems for hybrid virtual-physical immersion through augmentation of senses,” and, “design frameworks for data-driven augmented reality and virtual reality storytelling.”
While conceiving the meaning of “advanced visual capture and processing systems,” recall the CIA investment winner AWS Elemental drawing the spotlight to Supermicro in Bloomberg’s 2018 “The Big Hack.”
Legal clues into Microsemi
On December 12, 2023, Microsemi filed a civil complaint in the Northern District of California federal court against several defendants, one namely Jerry Chang.
Jerry Chang is a former employee of Microsemi from 2001 to 2016. As the defendant in the Complaint for Conversion, Breach of Contract, and Unfair Competition, Chang was accused of stealing Microchip’s designs for “global avionics, radar, and industrial applications.”
With a degree from UC San Diego, Chang was the director of transistor engineering for Microsemi’s RFIS Transistor Solution, managed the transistor engineering department, and led the product development team designing state-of-the-art high power transistors and modules for radar, avionics and communication markets.
While at Microsemi, Chang appeared on an EDI CON 2013 GaN panel in Beijing while Microsemi’s latest products were marketed for avionics applications including TPR (Transponder), IFF (Identify Friend and Foe), MDS (Mode-S), MDSELM, Data Link, radar applications like air traffic control radar, phase array radar, weather radar, long range radar, surveillance radar, medical radiation applications, and for communication markets, in general.33
By 2016, Microsemi were advertising their importance to the automotive navigation markets.34 It was still a fresh market for that focus of technology which only began commercially just before the time of Chang’s visit to Beijing.
These details will be important to keep in mind to grasp the breadth of the impact of the findings within this report.
Network-1 v. Fortinet
Microsemi themselves were also named in a 2020 lawsuit filed by Network-1 Technologies for claims of Fortinet’s own intellectual property theft of Network-1,35 but Microsemi were also joined by the networking industry’s top names including:
Alcatel-Lucent
Allied Telesis
Avaya Inc.
AXIS Communications
Cisco
Dell
Extreme Networks
Fortinet
GarrettCom
Hewlett-Packard
Huawei
Juniper Networks
Microsemi (Microchip)
Motorola
NEC
NetGear
Polycom
Samsung
Shoretel
Sony
Transition Networks
These companies were not all named as Defendants, but rather simply named in the filing as all utilizing the “930 Patent,” a patent for using “phantom power” across ethernet connections. These companies all do have one thing in common, however: Ethernet cables.
These companies either:
Use ethernet ports or switches in their own builds, or
Actually manufacture or distribute the switches themselves.
The April 17, 2001-filed 930 Patent is the underlying technology that enables remote server updates to be executed while a system is technically powered “OFF.”
An attacker with general knowledge of a system’s specifications could program malware to probe the ethernet switch’s status, activate it and the target hardware in the circuit, and upload malware to those components through the motherboard’s native, fully compliant, up-to-specs circuitry itself, all without ever turning the machine “ON.”
Network-1’s 930 Patent is claimed by the company to be the key patent behind the IEEE 803.2af and 802.3at designations, and is regarded as an industry-standard technology.
In 2010, University of Michigan professor Wei Lu founded a company called Crossbar, who later in May of 2018 agreed to collaborate on research, but for Microsemi to also license a special technology from Prof. Wei Lu.
The tech that Microsemi was leveraging from the U-Michigan professor allowed terabytes of “always-on data storage” to be embedded into any FPGA chip or processor.36
Storing the data to any chip on a motherboard for later access as opposed to transmitting it in real-time would circumvent packet monitoring techniques among other things; This would hypothetically leave data to lie in wait for the next large-scale “breach” of systems before being downloaded and secretively cleared from the not-so-secret memory modules where it was secretively stored.
The way this could be done easily is through the unprogrammed, throwaway “cells” on the FPGA portions of any ASIC (Application-Specific Integrated Circuit) chip.
Intel and Altera
In 2010, Intel Corporation, Arizona State University, and USAID partnered originally for $5 million in the Higher Engineering Education Alliance Program (HEEAP), but ballooned to $40 million by August of 2015.37
The partnership ran alongside Intel’s $1 billion investment into the Vietnam economy, announced some four years prior.38
FPGA giant Altera was acquired by Intel in 2015 for $16.7 billion and the Cyclone FPGAs were cycled out by the beginning of 2019.39
By 2018, Intel’s FPGA development had progressed to a point of these commercially common BMCs using FPGA cells that measured between 20 and 130 nanometers.40
Making the generally safe assumption that industry leaders in this specialized technology were remotely on par with these developments, this also matches the meandering descriptions of exactly what — physically — was the underlying risk of Supermicro boards in the 2018 Bloomberg BW article — FPGA chips.
Altera/Intel discontinued their Cyclone 1st-gen FPGAs (2003-2004) in 20184142, making it plausible that the 2018 Bloomberg BW “Supermicro story” was about a model of FPGAs already being phased out; This may also provide logic to why a “sampling” of Supermicro’s products returned no alarm, and may even reasonably shed light on Apple’s seemingly contradictory behavior in response to the Bloomberg firestorm.
Intel recently revived Altera as a stand-alone brand from Intel.43
Intel has a long-standing partnership with federal cybersecurity provider Fortinet.44
Fortinet
Fortinet’s entire suite of government and commercial cybersecurity products have been exposed to major security vulnerabilities for well over a decade. The list is long and widespread, with the world’s leading cybersecurity authorities taking notice and reporting since at least 2016.
In the DHS-funded Common Vulnerabilities and Exposures (CVE) database, a keyword search for “Fortinet” returns over 1,000 all-time hits.
Using the keyword “Fortinet” on USASpending.gov returns 551 results and nearly $70 million from the Department of Defense alone in all-time awards.
When looking at the U.S. cybersecurity picture as a whole, it comes as no surprise that many of Fortinet’s most critical vulnerabilities align with the timeline of major breaches of highly sensitive cyber infrastructure.
Fortinet and Supermicro
Fortinet designs its own ASIC (Application-Specific Integrated Circuit) chips branded “FortiASIC,” and also — at least since some point in 2015 — required Supermicro motherboards for its system to operate as designed on Brocade’s Vyatta routers.45
Regardless of Fortinet’s specific proprietary ASIC chip design, their systems also apparently use FPGA systems somewhere in their design, judging from a sample console log provided in FortiDDoS release notes,46 both of which would inevitably require firmware updates.
The late-2012-issued FortiASIC-SoC2 chip was reportedly the first “custom-architected FortiASICs,” indicating that Fortinet were building their own systems on top of existing hardware prior, but were now having their chips built to their own specs, however.47
A malicious entity with intimate or stolen knowledge of the proprietary designs would also know precisely how and where to pinpoint their effort. Regardless of who is to blame for Fortinet’s repeated security failures, the company employs an enormous amount of alumni of incredibly PLA-friendly university programs.
An internal Fortinet document explicitly states that FortiSIEM Hardware appliances are based on Supermicro appliances.48
Cavalcades of Vulnerabilities
There were dozens upon dozens of reported vulnerabilities in Fortinet products over the years, but several periods were noticeably more concentrated with vulnerabilities.
Found at CVE.org:
The keyword search fortinet authentication returned 28 results dating back to 2013.49
2013 may be significant to this timeline when considering Fortinet’s apparent continued involvement with its founders’ alma mater, Beijing’s Tsinghua University, indicated by a 2013 working group where representatives from the two bodies signed into a workshop together.50
The keyword search for fortiOS firmware returned two results.51
The keyword search for fortinet inject returned 36 results dating back to 2012.52
Seven results since 2015 for fortinet administrator.53
14 results for fortinet credentials since 2016.54
Important to note is that these vulnerabilities are not necessarily indicative of increased security breaches of their own products, but absolutely correlate often to other IT and commercial/government software products’ breaches.
2012
There were several reported vulnerabilities in Fortinet’s systems that reached back to 2005, but no year numbered quite like 2012 up until that point. From there, it was a steady increase in vulnerabilities reported, many by Fortinet themselves, until 2015 when the volume of reports markedly increased.

2012 was the year Fortinet launched its first “custom-built” ASIC chip on its systems.
The first U.S. Cybersecurity and Infrastructure Security Agency (CISA) advisory that affected Fortinet products (according to their public website) was issued 22 Aug 2016: “Fortinet Releases Security Advisory”
The advisory reported a patch issued by Fortinet for their products that dated back to 2012; In the acknowledgements it specified the original report was in fact made to the company also in 2012 — four years before the Aug 2016 patch.
Fortinet’s slide into chronic failure
2015 was a year of repeated intrusion and security lapses for Fortinet. Thirty-five keyword-searchable vulnerability alerts posted to CVE.org, to be exact.55

It was also a year of mass realignment within tech R&D, Silicon Valley capital investments, and the geopolitical landscape with the announcement of Donald Trump’s candidacy for President in June of 2015.
In 2015, the former two-term Governor of the State of Washington, Gary Locke, joined the Board of Directors of Fortinet.56
Equation Group specifically targets Fortinet
On August 18, 2016, Amol Sarwate at Qualys wrote that the “behavior of the [Fortinet] firewall is peculiarly interesting,” in his quick blog alert about a recent Equation Group hack that targeted the company’s products:57
“We were able to confirm the Cisco ASA (Advance Security Appliance) SNMP remote code execution issue…
We were also able to verify the FortiGate HTTP vulnerability which allows attackers to send a specially crafted HTTP request which can result in remote administrative access for attackers. The attack is based on E-tags in the HTTP request and the behavior of the firewall is peculiarly interesting.”
-Amol Sarwate, blog.qualys.com
Fortinet’s corporate “ancestors” also targeted by Equation Group
24 Aug 2016 — The Register: “Equation Group exploit hits newer Cisco ASA, Juniper Netscreen”5859
Both Fortinet founders, Ken and Michael Xie got their start out of Tsinghua University in Beijing with companies that intertwine with major companies’ mergers and acquisitions throughout the niche industry.
Ken Xie was the founder of NetScreen, another VPN company, which sold to Juniper Networks in 2004.
Ken Xie developed some of the first ASIC firewalls and VPNs.
Ken Xie’s brother, Michael Xie, was the Software Director and Architect for NetScreen60
Juniper was brought into question in 2015 over a purported FBI and DHS investigation into unauthorized code, alleged to be secretly embedded into their network systems.61 They, too, suffer vulnerabilities and attacks at the same frequency and sensitivity levels that others in the industry like Fortinet encounter.
Despite the vulnerabilities and breaches in cybersecurity, even those directly affecting Fortinet specifically, with each cascading event, the company benefits from Silicon Valley and cybersecurity industry investors.62 This pattern amongst the same group of companies — failure > crisis > solution > taxpayer/retirement/pension investment > windfall profit > failure > repeat — has been consistent across the entire technology economy for two decades.

The NSA itself joins the fray — 2017
In January of 2017, Former NSA Cyber Task Force Executive Phil Quade was named Chief Information Security Officer of Fortinet.63
Some four months later on May 15th, Fortinet announced the former Director of both National Intelligence (DNI) and the National Security Agency, Mike McConnell, to be joining the Board of Fortinet Federal, the brand new government-exclusive security service. Also joining in on the lateral moves were former Washington State Governor and former Secretary of Commerce, Gary Locke and, again, former NSA executive Phil Quade.64
Taking a step back to reconsider the prior findings of so many tech researchers all coming to the common conclusion that the United States’ own NSA was seeding malware worldwide, it squares in shocking fashion to the repeated intrusions and incursions that began plaguing Fortinet after the former NSA execs joined the team.
2018 — Present
Beginning around 2018 with addition of former NSA execs and a member of a Chinese elite organization (more on that shortly), the frequency, volume, and severity of the vulnerabilities reported by Fortinet were monumental, with an even sharper uptick from 2022 and onward.

3 Jan 2018 — CISA: “Meltdown and Spectre Side-Channel Vulnerability Guidance”
Fortinet among others named vulnerable in the CISA advisory65
16 Mar 2018, six months before the Bloomberg Supermicro article about “backdoor chips” — Cybersecurity and Infrastructure Security Agency (CISA): “Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors.”
Advisory was pre-dated to prior malicious activity in March of 2016.
Fortinet among others were named vulnerable.
6 Jul 2018: Fortinet issued CVE-2018-13379: “...SSL VPN web portal allows an unauthenticated attacker to download system files via special crafted HTTP resource requests.”
7 Jan 2019 — Fortinet issued CVE-2019-5591: “A Default Configuration vulnerability in FortiOS may allow an unauthenticated attacker on the same subnet to intercept sensitive information by impersonating the LDAP server.”
6 Sep 2019 — TomsHardware.com: “State-Sponsored Chinese Group Hacks Enterprise VPN Servers”
The article names FortiOS specifically as “targeted.”66
12 May 2020 — Fortinet issued CVE-2020-12812: “...user being able to log in successfully without being prompted for the second factor of authentication (FortiToken) if they changed the case of their username.”
2 Feb 2024 — Fortinet reported a threat level 9.8 for an externally-controlled format string at the operating system-level that “allowed an attacker to execute unauthorized code or commands via specially crafted packets.”
Fortinet and Salt Typhoon
Just as recently as 10 weeks ago, Senator Chuck Grassley demanded a detailed report from Fortinet CEO Ken Xie to address the company’s lapses and failures in protecting the federal government’s critical systems.67
Subsequently six weeks ago, Rob Rashotte, Vice President of Fortinet Training Institute, delivered written testimony to the U.S. House Committee on Homeland Security Hearing with the header, “Preparing the Pipeline: Examining the State of America’s Cyber Workforce.”68
This may seem counterintuitive when taking a step back to examine exactly the talent base that all of Silicon Valley utilizes, including Supermicro, Fortinet, and Arizona company Microchip utilize, while leveraging nonprofits for additional institutional support.
Truth and Consequence
It goes without saying for international companies tied to multiple governments that the talent pool is undoubtedly vast, diverse, and global. For such diversity, there are certain, undeniable tendencies of companies’ hiring practices that mirror those at Ivy League and “Public Ivy” universities of late.
Arizona State University
At the top of the Arizona State University chain of command is Dr. Michael M. Crow since 2002.69
ASU President Michael Crow
Any conversation about Arizona State University and government has to be accompanied by a conversation about ASU President Michael Crow. Before Arizona State, Crow was at Columbia and before that, Iowa State University.70
As Director of the Office of Science Policy and Research at Iowa State University in 1985, Crow likely brushed elbows with a prodigious 12-year-old boy named Steve Hsu.
“I actually took my first college course (in the comp sci department -- punch cards!) when I was 12.”
-”School daze,” Steve Hsu
(https://infoproc.blogspot.com/2010/11/school-daze.html)
That child’s name was Stephen (Steve) Hsu, a future scientific advisor to BGI Genomics and the Vice President of International Affairs and Research at Michigan State University (2013).71
Crow was also the Program Development Coordinator of the Fossil Energy Program at Ames National Laboratory for the U.S. Department of Energy at Iowa State University from 1977 to ‘78, indicating that Crow was also in town at the time that Hsu was 12 years old and taking classes at Iowa State.
“When I was a high school student I took advanced physics courses at the local university. One of my professors suggested I look at the Feynman lectures for more challenging material. I ordered a set (paperback, with red covers) through the university bookstore — I think they cost $30 in 1982.”
-Feynman Lectures: Epilogue, Stephen Hsu
https://web.archive.org/web/20150127162331/https://spartanideas.msu.edu/2014/12/07/feynman-lectures-epilogue/
Michael Crow has been on the Board of Directors of the Central Intelligence Agency’s official “nonprofit” investment firm, In-Q-Tel, since its inception, and has been the Chairman of that Board since 2006.
Verifiably in 2003 and likely since, Arizona State University President Michael Crow was partnering with the CIA to develop surveillance technologies.72
Steve Hsu’s startup company, SafeWeb, was the recipient of an In-Q-Tel investment early in its history, and was accused of its own data insecurities as a VPN service in 2002.
Hsu made no bones about the situation to Wired Magazine that the CIA was aware of the vulnerabilities despite their inaction:
"They were aware of these capabilities but they did not deem it to be a threat."73
Michael M. Crow also served on the Arizona State Board of Education (2003-07, 2015-16), is currently on the International Advisory Council for the American University of Beirut in Beirut, Lebanon (since 2019), and since 2021 has been on the Strategy, Innovation and Technology Committee at the Smithsonian Institution, and the Board of Directors of the Los Angeles Area Chamber of Commerce.74
Under Crow’s leadership, Arizona State University established a Confucius Institute in partnership with Sichuan University in Sichuan, China in 2007, just after rising to Chair the Board of In-Q-Tel.75
Arizona State is a main supplier of talent for many in the computing and semiconductor world. Phoenix is a self-proclaimed hub for Silicon Valley’s U.S.-based supply chain.
Intel’s Altera sponsored ASU’s Prof. Fengbo Ren
Altera, too, was and remains an industry partner of Arizona State University and directly supported the Fengbo Ren Lab at the school.76 In fact, at the time of the Intel acquisition of Altera in 2015, Arizona State and Fengbo Ren were recruiting graduate students who had hands-on experience with Xilinx and Altera FPGAs.77
Dr. Fengbo Ren is a 2014 Ph.D graduate of UCLA — a major player in the University of California system — with a 2008 B.S. in Electrical Engineering from Zhejiang University in Hangzhou, China.78 These two details are monumentally important when taken together.
Ren was an exchange student from Zhejiang University to Hong Kong University of Science and Technology (HKUST) in the 2006-07 academic schoolyear.79
This also means that Fengbo Ren learned from an academic at HKUST who has proven to be one of the most consequential people in the world to this specific story — Dr. “Lionel” Mingshuan NI. That particular avenue of investigation calls for an entirely separate inquiry for another time.
Flatfooted Feds
In 2015, the FBI declared China’s C9 League — the “Ivy League” of China — a risk for espionage and intellectual property theft through Chinese talent programs, but also U.S.-based professional and alumni organizations, more often than not, directed or heavily influenced by Beijing.80
Since that declaration, more schools and organizations have proven themselves to be sources of espionage and intellectual property theft, drawing the ire of Congress and the American public. In most cases, China is keen to retain close relationships with its C9 League alumnus abroad, through any avenue available to the intrusive government.81
None of this skepticism nor criticism, of course, has been angled under the potential premise of the U.S.’s complicity and participation in that very activity.
Ren’s background is specifically around embedded systems, like those that run on ASIC chips, and his work covered FPGAs while interning at Qualcomm, Cisco, and Broadcom — all industry staples.
Since at least 2005, Zhejiang University and HKUST have collaborated, as all things in China do, to support the Hong Kong Science and Technology Park in an integrated circuit trading platform.82
In 2020, Mike Pompeo announced to Congress that the Trump Administration no longer considered Hong Kong to be autonomous of the People’s Republic of China.83
Zhejiang-California International NanoSystems Institute (ZCNI)
Zhejiang University also operated the Zhejiang-California International NanoSystems Institute in partnership with the State of California, UCLA, and UC Santa Barbara,84 established in June of 2005.85 It continued operation to some degree through at least 2021, though paperwork indicates their operating from ZJU’s home in Hangzhou.86878889 ZCNI had several members of the Chinese Academy of Sciences on its Advisory Board in at least 2013.
The Institute in 2019 hosted their fifth gene editing seminar, based on CRISPR technology.90 The Zhejiang California Nanosystems Institute’s website is still in operation today, though it seems the formal affiliation with CNSI ended after the 2016 election.91
Zhejiang University is largely the epicenter of China’s automotive R&D, and shoulders more than its weight of GPS, mobile networks, cryptology, and semiconductor research.
The lab was part of the greater California NanoSystems Institute (CNSI) that continues today, but even as recently 2023, delegations of Zhejiang University and UCLA “reflected on a decade of cooperation” which undercuts the notion that their affiliation ended in 2016, and pledged to strengthen ties further.92
This decade of cooperation eluded to well over a decade, 18 years to be exact, of cooperation between the two schools through the 2005 establishment of ZCNI, but also a 2009 agreement to transfer 1500 patents from UCLA into Mainland China through Zhejiang University.93
ZJU’s faculty includes 26 members of the Chinese Academy of Sciences, 27 members of the Chinese Academy of Engineering, 164 Chang Jiang (Yangtze River) Award winners, and 154 recipients of the awards from the National Science Fund for Distinguished Young Scholars.
ZJU is also home to eleven “State Key Laboratories,” labs who carry out the most crucial research for China’s military and most sensitive national science objectives.
ZJU-Hangzhou Global Scientific and Technological Innovation Center
An inevitably critical piece to the story is Zhejiang University’s ZJU-Hangzhou Global Scientific and Technological Innovation Center, established in 2019,94 just miles away from Zhejiang University’s joint-institute campus with the University of Illinois at Urbana-Champaign, the ZJU-UIUC Institute, which was approved by the Chinese Ministry of Education in February of 2016.95
The ZJU-Hangzhou Global Scientific and Technological Innovation Center paved the way for Zhejiang University’s Advanced Semiconductor Institute program to begin in 2021.9697
“At present, [ZJU-Hangzhou Global Science and Technology Innovation Center] conducts substantial cooperation with top universities, e.g. Harvard University, Yale University, Oxford University and Cambridge University in major research fields, joint programs with Ecole Polytechnique, Paris and University of Toronto, Canada, etc. in talent cultivation…”
-ZJU-Hangzhou Global Science and Technology Innovation Center, as of March 31, 202598
Zhejiang University collaborates with Tsinghua University in Beijing through at least one science park in Hangzhou, and with the People’s Liberation Army through the 2017 MOE Civil-Military Innovative Research Center for Micro-Satellite and Constellation.99
Did China infiltrate the “Five Eyes” or simply build it?
With so many instances of the United States’ national security apparatus declining to act, even outright covering up major security vulnerabilities in the nation’s systems, it cannot also be reasonable to expect this same apparatus to act behind the scenes to deny visas or alert background checks into the tech industry’s foreign talent pool.
Neither Supermicro, Fortinet, nor Microsemi/Microchip are shy to seek hires from universities with military ties to China. There is a clear preference to pull talent from specific universities, shown across both companies, and for clear reasons that must include those programs’ affluence with military-grade cyber-systems development.
In China, the “Seven Sons of National Defence” is a group of seven universities who focus on contributing science and technological development directly to the People’s Liberation Army. Those seven universities are:
Beihang University in the Haidian district of Beijing;
Also nearby Beijing Institute of Technology;
Harbin Institute of Technology in Harbin, Heilongjiang;
Harbin Engineering University, also in Harbin;
Nanjing University of Science and Technology in Nanjing, Jiangsu Province;
Nanjing University of Aeronautics and Astronautics, also in Nanjing;
and Northwestern Polytechnical University in Xi’an, Shaanxi Province.
The Hoover Institution says they "operate as prime pathways for harvesting US research and diverting it to military applications."100
Keep these schools in mind while browsing the illustrations in this report.
Oh So Tangled Webs

Li Yunjie 李运杰 — Supermicro 超微电脑股份有限公司
李运杰 (Li Yunjie, sometimes Li Lunjie) has been the General Manager since 2005 of Supermicro’s Beijing headquarters, according to LinkedIn and reliable public access information in China.101102
According to the same profile devoid of any activity, Manager Li only lists graduating from Jilin University with a B.E. (工学士) in Electronic Information Engineering (电子信息工程) in 2001. There is no mention of any further education on the LinkedIn profile.
Jilin University has official PLA and Russian ties
The Chinese university tracker tool at the Australian Strategic Policy Institute (ASPI) website names Jilin University as a Mainland China university posing a “Very High” risk due to defense research and China’s nuclear program.103
Jilin University is a member of a non-governmental organization (NGO) called Association of Sino-Russian Technical Universities (ASRTU). They’re composed of “elite engineering universities of China and Russia on a voluntary basis,” according to their website.104
It is very common for affluent or successful alumni of Chinese universities to remain very connected to their Mainland lives through talent and alumni associations that promote Chinese culture, language, and cooperation.
Alex Hsu’s missing link
Though Li Yunjie is listed as the General Manager of Supermicro’s Beijing enterprise, Alex Hsu was listed as the Executive Director of Supermicro Technology (Beijing) since August of 2009.105
What may make this suspicious is the omission of this specific disclosure in any other official filings or correspondence on the EDGAR database on behalf of Super Micro Computer.
Supermicro reported in SEC filings that they deployed “dual processor server solutions” for Chinese computer manufacturer Dawning between 2007 and 2009. The next year, 2010, Supermicro began reporting leasing commercial space in both Beijing and Shanghai.
Supermicro says in SEC 10-K reports since 2010 that they have leased commercial space for since at least 2007.
Curiously, only in 2014 did Supermicro report leasing commercial space in Dongguan, Guangdong province. Dongguan is situated exactly between the tech research powerhouse city of Guangzhou and the tech manufacturing powerhouse city of Shenzhen; All in the Pearl River Delta, all mere dozens of miles inland from the banking and finance powerhouse of Hong Kong.
In 2020, Mike Pompeo announced to Congress that the Trump Administration no longer considered the Hong Kong Special Administrative Region (Hong Kong SAR) to be autonomous of the People’s Republic of China’s (PRC) central authority.

Checking all the boxes
To the real overarching point of our story here, one particular employee of both Supermicro and Fortinet checks multiple boxes for red flags in this timeline so far.
According to LinkedIn, with a 2006 B.S. degree in “Automation” from Tsinghua University, they are now the Principal Hardware Engineer in the “San Francisco Bay Area” since July 2012 at Fortinet and was a hardware engineer at Supermicro for nearly two years between November 2010 and July 2012;106
This is precisely when tampering was reported by Bloomberg BW to have begun at Supermicro, and also when an FBI investigation was reportedly opened into them (and so far, buried).
The employee is a Tsinghua graduate like so many other key players to Fortinet, in general:
Ken and Michael Xie, founders of Fortinet;
The VP of ASIC Product Engineering at Fortinet;107
The Sr. Director of ASIC Engineering at Fortinet;108
And an architect of ASIC design at Fortinet who was also a Tsinghua professor on wireless communication technologies between 1996 and 2000.109
Unholy Triumvirate

Xidian University
Another school the ASPI names as a “Very High” risk for espionage and intellectual property theft is Xidian University in Xi’an, Shaanxi, China110 with a key role in the PLA’s cyber program, whatever that may be,111112 along with other direct relationships with the People’s Liberation Army.113
“In 2011, Xidian University and CETC jointly established the Collaborative Innovation Center of Information Sensing and Understanding…. The centre’s partners include the former PLA General Staff Department’s Third Department…, other PLA units and research institutes, and state-owned defence conglomerates.
Xidian University began cooperating with Guangdong Information Technology Security Evaluation Centre (ITSEC), a division of the Ministry of State Security (MSS) 13th Bureau, in 2017. The university also collaborates with other divisions of the MSS 13th Bureau, including the Shaanxi ITSEC, with which Xidian University established a joint research laboratory and internship program in 2017.”
-Australian Strategic Policy Institute (ASPI)
Another important “Key Lab” at Xidian University is the National Key Discipline Laboratory of Wide Band-gap Semiconductor.114115116 Key Labs are known research conduits for the PLA to perform and access academic research for militaristic purposes.
In total, Xidian is connected to five national defense laboratories, according to ASPI.
Beijing University of Posts and Telecommunications
One more school in this trifecta is Beijing University of Posts and Communications, based in China’s “Silicon Valley” in the Haidian District of Beijing.
All told, Beijing University of Posts and Communications hosts to two national defense “Key Labs,” according to ASPI.117
The Space Between
Fortinet, Supermicro, and Microsemi/Microchip rely heavily on leadership taught by universities not only sympathetic to, but cooperative and close with China’s 3 million active and reserve duty, and paramilitary, not to mention the countless millions likely contributing intelligence in other roles, whether in academia, business, finance, or industry.
Their common taste for Xidian University is worth noting, however, the confluence of Beijing University of Posts and Telecommunications is nothing short of breathtaking when considering the subject of this report.
BESTI
Beijing Electronic Science and Technology Institute (or BESTI - the institute has an enrollment of a mere 2,000 students with stringent political requirements for admission) partners with Xidian and Beijing UPT as their primary research contributors, according to ASPI.
BESTI relies heavily on Beijing University of Posts and Telecommunications and Xidian University for research contribution118, as they are the two principal parties of the Communist university.
BESTI is probably best described as the Communist Party of China’s private technology institute.
Zhejiang University
Zhejiang University naturally has a contribution to the PLA as one of the world’s top semiconductor programs, shown in their own literature from around the time these elevated incursions began — 2016.119
According to ASPI, Zhejiang University is a “High” risk level due to their hosting three national defense-facing institutes.120121122123
Among those is one mysterious Key Lab for “Control Science and Engineering,” with ZJU’s public announcement reading as vaguely as the anglified name’s insinuation.124
All three vector-companies for repeated, targeted malware attacks — Supermicro, Microsemi/Microchip, and Fortinet — employ Zhejiang University alumni in various positions.
Microchip in particular has a notable concentration of Chinese talent from Zhejiang University, but also from PLA-linked programs working on its ASIC/FPGA technologies — a prime target for malware manipulation — but more importantly, the focal point of this report and their role as the nerve center for the quite apparent compromise of American cyber infrastructure — Tsinghua University

One particular engineer, Fred Yu, now a “Sr. Technical Sales Engineer” since 2012 for a Microsemi subsidiary according to LinkedIn, was for a handful of weeks in 2005 a “senior software engineer” for TopSec, a Chinese firm who in 2009 The Guardian reported that provided “...services and training for the PLA and has recruited hackers in the past.”125
Several employees are graduates of the Seven Sons of National Defence in China - seven schools who are established in no small part to directly support the PLA’s ambitions in every material way.
Worth highlighting is the overwhelming tendency to hire these highly questionable graduates to offices outside of the United States, particularly in Canada.
This report’s use of a “sampling” of employees who publicly posted their information to the website LinkedIn also provides a glimpse into these same individuals’ work histories, vividly exposing the trail of possible PLA-trained employees working within the entire American supply chain — even from neighboring countries.
Consequence of Truth
The Chinese military has very likely already quietly built “backdoors” by simply hiding tiny, otherwise benign pieces of the not-yet-assembled attack not only in the hardware, firmware, and software, but in the supply chain itself: From product conception and design, continuing through manufacturing, programming, and integration, and the finishing process through assembly, marketing, sales, and continuing product support via regular software and firmware updates.
A primary concern from this should be the severe implications to civil liberties and privacy in America; Other, more probable concerns would likely question the very legitimacy of many institutions and governments worldwide who have leveraged these covert systems to methodically seize power and amass untold wealth.
But furthermore, the NSA has not only turned a blind eye, former leadership of the Agency is contributing to what is essentially the Five Eyes (U.S., Canada, U.K., Australia, New Zealand) covertly spying on the globe using the joint-monopoly on computing hardware, globally, controlled and maintained by the unwritten Sino-U.S. cooperation.
Fortinet’s board reorganizes with increased security flaws
Fortinet underwent a shuffle in corporate leadership just as the first significant spat of vulnerabilities began being reported of the company in 2012.

Now-former Fortinet Board member, UC Berkeley professor and alumni, and former Taiwan Semiconductor Chief Technical Officer Chenming Hu was inducted to the Chinese Academy of Sciences as a foreign member in 2007,126 three years after leaving Taiwan Semiconductor to return to Berkeley.127
Chinese Academy of Sciences
The Chinese Academy of Sciences operates over 100 research institutes and 2 universities while supporting over 70,000 full-time employees and nearly 80,000 graduate students. Recently, the University of the Chinese Academy of Sciences were included in C9 League meetings, though not formally inducted as a member.128
On the Board of Fortinet, Ming Hsieh replaced a member of the Committee of 100, an elite U.S.-based Chinese NGO with deep ties to both Beijing and the U.S. national security establishment, a member by the name of Pehong Chen.
Pehong Chen is another UC Berkeley and Stanford alumni who is also on the UC Berkeley College of Computing, Data Science, and Society (CDSS) Advisory Board, is the former Vice Chairman of the Committee of 100, and a former Board member of the Mainland China-based Sina Finance.129
Talent and Professional Organizations
The programmatic underpinning that contributes largely to these university graduates’ flourishing in America is the same social and cultural fabric that keeps Beijing’s U.S. visa holders in touch with the Mainland and offering employment opportunities while in the States: “Promoting Chinese culture and language in America.”
CASPA
Founded in 1991, the Chinese American Semiconductor Professional Association (CASPA) touted itself in 2000 as the “largest Chinese American semiconductor professional organization outside of Mainland China and Taiwan.”130
The 501(c)(3) said also in 2000 that they are a, “nonprofit, membership-based organization that assists individuals and enterprises in the semiconductor related industries to achieve their personal goals and the organizational effectiveness, the primary sustainable competitive advantage in a global economy.”
In 2002, CASPA’s Austin chapter listed board members with company email addresses from Dell, Intel, Applied Materials, Silicon Labs, Motorola, Taiwan Semiconductor, and the University of Texas.131 By 2008, CASPA advertised, “more than four thousand individual members covering multiple disciplines,” and that, “Most of them are semiconductor professionals working in Silicon Valley, Southern California, Oregon, Washington, Arizona, Texas, New York, China, Taiwan, and Singapore.”132
CASPA in 2008
To only halfway emphasize the longevity of this business model, CASPA in 2008 is a prime example of the talent pool that companies like Supermicro, Microsemi/Microchip, and Fortinet have to select from.
Some of CASPA’s top-tier sponsors in 2008 included Hong Kong Science and Technology Parks, Microsoft, Shanghai Zhangjiang Hi-Tech Park, and Taiwan Semiconductor.133 Other 2008 sponsors included Intel, Qualcomm, Deloitte, Shanghai Hua Hong NEC Electronics Company, Hangzhou Xiaoshan International Innovation Center, the Chinese State-owned Suzhou Nanotech Co. Ltd., Anyang National New and High-Tech Industry Development Zone, SIASUN Robot & Automation Co., and SMIC. 134135136
CASPA chapter Chairs in 2008 were employed at major tech firms, specifically: Dell, Inc., Texas Instruments, Redrock Semiconductor, and two from Taiwan Semiconductor.137138
There is even a CASPA Chapter for the Pearl River Delta,139 which encompasses the cities of Hong Kong, Macao, Shenzhen, Dongguan, Guangzhou, and Zhuhai. If the Pearl River Delta isn’t deep enough into the Chinese market, a chapter in Shanghai gives CASPA a direct line.
The chair of the Shanghai chapter was listed on their website as a Vice President at Shanghai Huahong Microelectronics Co.,140 a company that is now China’s second largest chipmaker.
CASPA Silicon Valley’s chapter Chair was with Taiwan Semiconductor (TSMC) in 2008,141 and the chair of the Phoenix chapter of CASPA was from the staffing company ATD.142
Like American unions, the nature and purpose of these types of professional associations is to advocate for its members and to offer benefits by banding together as a group. Unfortunately, this has proven for an extended time to provide bad actors with ample opportunities to try to blend into the crowd and commit espionage by selling American secrets.
CASPA in the “Big Data” era
By 2016, the group’s sponsorship and corporate connections back to Mainland China exploded into nearly full integration with the Chinese tech industrial base. Sometime around 2019, FPGA inventors Xilinx were listed as members, and their badge on the website was surrounded entirely by Chinese companies and one other FPGA chip maker.143
Huawei, Taiwan Semiconductor, and Applied Materials were listed at the top of the 2016 archived webpage.
This even continued through 2022 in round-about ways with top-tier sponsors like Futurewei, Huawei’s North American research arm despite Huawei being on the U.S. Entities List, or data storage company Yangtze Memory Technologies in Wuhan, China144, or platinum (second-tier) sponsor Shanghai-based FPGA chip designer MooreElite 摩尔精英.145
By 2024, Supermicro and Hong Kong Science and Technology Parks were listed as diamond (third-tier) sponsors of CASPA.146
Danny Hua is a longtime Huawei executive and has been on the Board of Advisors to CASPA’s Silicon Valley headquarters, according to his LinkedIn.147 Public Form 990s filed with the IRS confirm him on the board in 2012148 culminating in 2018 as president of the organization and subsequently disappearing from tax filings.149
Huawei was banned from operating in the United States by President Trump in 2019. Futurewei is technically a distinct company from Huawei, but both ultimately serve the same beneficiaries, none among those being American national security.
CASPA Phoenix
The 2016 CASPA chapter in Phoenix is a window into the interconnection of the Chinese workforce within the American academic and industrial base.
Larger entities represented by individuals in their leadership of the Phoenix chapter include many of the chief entities of this report, including a Chinese government agency ([Chengdu] Municipal Science Technology bureau), ATD, Rocketwell, Microchip, Intel, and Arizona State University.
CASPA now
CASPA is now led by Dr. Zhibin Zhao, a founding team member of Alibaba’s chip business unit who built their first AI chip, and a graduate (B.S. ‘03, M.S. ‘06) of Zhejiang University and UC Davis, who is part of the Fudan-UC Center partnership.
Chinese Institute of Engineers (CIE)
According to a 100th Anniversary CIE brochure,150 the Chinese Institute of Engineers was first proposed in Cornell, New York on Christmas Day in 1917. Shanghai, China soon became the headquarters for the group with New York becoming a chapter of the organization.
In 1979, the group reorganized and a San Francisco chapter (for Silicon Valley) and with the newly reformed Greater New York chapter, established a “National Council” of a federation of the combined chapters.
In 2002, CIE began awarding the Asian American Engineer of the Year Award (AAEOY) to outstanding Asian engineers in industry and the academic community.
In the years since, other chapters have been established in New Mexico, Southern California, Dallas-Ft. Worth, Seattle, and even a chapter for overseas engineers called Overseas Chinese Environmental Engineers and Scientists Association, or OCEESA.
CIE-San Francisco
The CIE 2008 National Council included a founding member and the second president of CIE-SF, Y.C. Yang.151 Also listed in the publication was Jonathan H. Chao in leadership with the group’s Greater new York chapter.
Y.C. Yang passed away in 2016, memorialized by the Committee of 100,152 of which he was also a founding member in 1990. He had remained an advisor of the organization up until the time of his death.
Other members of both CIE-SF and the New York-based Committee of 100 included another former Fortinet Board member Pehong Chen, the founder of Lam Research David Lam, and Fortinet founder, CEO, and Chairman Ken Xie.
CIE-Greater New York and Jonathan H. Chao
CIE-SF connected Ken Xie to ASIC engineer Jonathan H. Chao and New York University where Chao performed several research projects with academics from Tsinghua University, but also Fortinet, specifically. NYU’s Jonathan Chao is a former chapter president and a lifetime member of CIE.153
Jonathan Chao is named co-author of 17 publications with Fortinet’s Junjie Zhang, on 71 publications with a researcher named Zehua Guo from the Beijing Institute of Technology, and appears in 13 publications with Minghao Ye154 — another Huazhong University of Science and Technology alumni who has now been a software engineer at ByteDance/TikTok since June of 2024.155
According to ASPI, Beijing Institute of Technology hosts ten of China’s major defense labs.156 It is one of the Seven Sons of National Defence of China.
According to ASPI, Huazhong University of Science and Technology is also a “Very High” risk due to their six national defense labs and other direct connections to the People’s Liberation Army.157
One particular study published in 2021, “Federated Traffic Engineering with Supervised Learning in Multi-region Networks,” looked into “geographically distributed network[s]” like the Google Cloud and how to integrate artificial intelligence into managing their network traffic across the dispersed network.158
The research was funded by the:
“Key-Area Research and Development Program of Guangdong Province under Grant 2021B0101400001, the National Natural Science Foundation of China under Grant 62002019, and the Beijing Institute of Technology Research Fund Program for Young Scholars”
-”ACKNOWLEDGMENTS,” Federated Traffic Engineering with Supervised Learning in Multi-region Networks
“For his dedicated service to [the] Institute,” Dr. Jonathan H. Chao of NYU was given the Chinese Institute of Engineers-USA Achievement Award in 2009.159
“Supermicro Intelligent Technology (Beijing) Co.”?
Interestingly, there has been another researcher/student at Tsinghua University who on his personal webpage cites his project “emNavi” — embodied navigation — as a collaboration with a secretive Beijing company that shares a lot of common characters with another name when spelled in Chinese: Supermicro.160 Some Chinese search engine results sometimes show Kangyao Huang as a representative of that company, as well as sometimes interpreting Supermicro as “AMD” — Advanced (Super) Micro (Micro).
Research published by Kangyao Huang indicates the emNavi project was in part from collaboration with the University of Michigan, where former Arizona State professor Jieping Ye joined the faculty in 2015.161
The researcher from U-Michigan even used a Mainland China-based email address, drawing into question what data at University of Michigan may have been absorbed by the intrusive CCP during the course of this project.
Aside
U-M’s Jieping Ye was succeeded after leaving Arizona State University in 2010 by his former student, Jiayu Zhou, who then arrived at Michigan State University in 2015; He recently rejoined Jieping Ye at University of Michigan in August of 2024.
Before Zhou rejoined his former mentor and while at Michigan State University, Jiayu Zhou ran a federally funded computing cluster called ILLIDAN from 2015 to 2021. This computing cluster contributed its resources to this same cohort through the University of Southern California, UC Santa Barbara, New York University, University of Illinois, and University of Michigan. The collaboration openly included many top Chinese firms like Pony Ma's Tencent, JD.com, and a prominent Chinese "Uber" service called DiDi.
The University of Michigan recently shuttered its DEI offices after ending its research agreements with Shanghai Jiao Tong University.
After the Jiayu Zhou vacancy at Arizona State in 2015, in came (Cao) Kevin Yu returning from Kyoto, Japan. Kevin Yu is a graduate of CCP darling Peking University and earned his PhD from Chenming Hu at UC Berkeley in 2002.
According to his own curriculum vitae, Kevin Yu was given the Chunhui Award for Outstanding Oversea Chinese Scholars in 2008. This award for Yu’s participation under a Chinese scholarship program known for espionage came following an extra year at Berkeley after his PhD, and three years at Arizona State, whose President was and is the CIA and In-Q-Tel’s Michael Crow.
Asian American Engineer of the Year Awards
The CIE-USA gives an annual award recognizing “outstanding Asian American professionals in Science and Engineering for their technical, leadership and public services achievements.”162 Every year it is littered with scientists across the entire defense industry and critical infrastructure.
In 2011, Chinese Academy of Sciences foreign member and National Medal of Technology and Innovation recipient, CIE member Dr. Chenming Hu was awarded the Distinguished Lifetime Achievement award by the group.
In 2013, Dr. Subra Suresh of the National Science Foundation (soon to be President of Carnegie Mellon University and a 2016 Chinese Academy of Sciences foreign member) was also honored with the same award.
NVIDIA founder and President Jensen Huang was given the honor for 2020-2021.
Chinese Academy of Sciences and Subra Suresh
In 2016, the Chinese Academy of Sciences inducted Carnegie Mellon University President Subra Suresh as a foreign member.163 In 2016, Suresh was also the President of Carnegie Mellon University in Pittsburgh, an infinitely consequential institution to the United States cybersecurity apparatus.
Carnegie Mellon University’s CERT Division is one of the several mechanisms behind CISA’s chief watchdog, CERT.164 The name “CERT” is in fact a registered trademark of Carnegie Mellon University.165 Carnegie Mellon University and Tsinghua University offer a joint Computer Science degree.
Stanford University
Fortinet founders and Tsinghua University alumni Ken and Michael Xie have their own 501(c)(3)-status nonprofit Xie Foundation which has donated well over $100 million to Stanford University alone in the last decade, as well as some to one of many of Ken and Michael Xie’s alma mater Tsinghua University’s alumni nonprofits.
This nine-figure contribution to Stanford bought a leading government/defense contractor two chair professorships in a formal position called the Fortinet Founders Chair Professorship.
Fortinet Founders Chair Professors
Pamela J. Hinds is the Fortinet Founders Chair of Management Science & Engineering at Stanford University, a position whose founding holder was Elisabeth Paté-Cornell,166 who was on the Board of the CIA’s investment arm, In-Q-Tel, with Arizona State University President Michael Crow until 2017. Paté-Cornell still remains on the faculty in the same department under Hinds.
The second Fortinet Founders Chair professor is Dr. Yi CUI, a renowned and well-tenured professor across different focuses in energy and materials science, but also ecology and chemistry. Cui was named the world’s “most influential scientific minds” by Reuters in 2014 and ‘15, a timely piece to attract wealthy research donors.
Dr. Yi Cui received his PhD as a student of Charles Lieber, the Harvard professor of nanoscience who was arrested in 2019 and eventually convicted and imprisoned over his lying about his involvement in the Chinese Thousand Talents Plan for overseas scholars.167
Cui received his PhD under Lieber in 2002, the very same year that the American Zhu Kezhen Education Foundation (AZKEF) sent Lieber to Zhejiang University for an academic lecture as part of their “Distinguished Lectureship” series (more soon).
AZKEF is Zhejiang University’s U.S.-based alumni organization that was at most points managed directly by the university itself, if only through backchannels.
Perhaps one reason the FBI and DOJ have been reluctant to pursue any type of meaningful legitimate action against this activity could be that they, too, have benefitted from this arrangement to some degree.
While Ming Hsieh was still CEO of Cogent Systems in 2009, one of the leading biometric researchers who worked in the lab to which Hsieh donated, Anil Jain at Michigan State University, was sent in 2009 to Beijing for a three-year adjunct professorship that coincided with the launching of another one of China’s “Overseas Experts” talent plans and followed the same timeline.168
Jain performed multiple projects with the CITeR Lab at WVU, of which Ming Hsieh was a major contributor. The CITeR Lab is essentially the FBI’s and National Institute of Justice’s identification technologies lab.
When Dr. Jain returned to MSU around 2012, he arrived to an outgoing Vice President of Research at MSU for the incoming BGI Genomics’ scientific advisor Stephen Hsu.
Dr. Anil Jain was inducted into the Chinese Academy of Sciences as a foreign member a decade after beginning his professorship at Tsinghua, in 2019.169
Ming Hsieh’s passive role in IP transfer
The University of Southern California renamed its graduate school’s Electrical Engineering department in Hsieh’s namesake in 2006 after a significant contribution, and opened the Ming Hsieh Cancer Institute in 2010, after a $50 million donation, and subsequently launching his own for-profit genetics company, Fulgent Therapeutics.170
Hsieh is a member of the Committee of 100, on the Board of Trustees at USC, but also at Fudan University in Shanghai after significant contributions of hard capital.171172 Every graduate with an M.S. in Electrical Engineering from the University of Southern California since 2006 bears Ming Hsieh’s name on their degree.
Hsieh is also an alumni of the University of Southern California, but according to a “Factpedia” entry to the Chinese service, it plainly states Hsieh transferred to USC from what is now called the South China University of Technology in the now-rising tech hub city of Guangzhou, China.
It should also be noted that the claim is uncited. However, it’s a definitive statement that can easily be verified or discredited through official channels; It could be critically important to understand how Hsieh came to be in America, as this area specifically was rife with “illegal” likely PLA-sanctioned activity in the underbelly between the Hong Kong’s tech and finance and Guangdong Province’s manufacturing base in the 1980’s and 1990’s (see: Chinese billionaire Wang Wei173).
Biometric surveillance tech co-op
Cogent Systems founder and former CEO, now-Fortinet Board member Ming Hsieh donated over $56 million to the University of Southern California (USC) where he’s a Trustee, but also millions to Stanford University alongside contributions to Fudan University and additional donations to Fudan University’s education fund, registered at the same address of UC-San Diego on Gilman Drive.
After donating $10 million to Fudan University in 2011,174 Ming Hsieh joined the Board of Trustees at Fudan where he remains today. Relevant to this same timeline, Jonathan KS Choi also joined this same Board175 after his own $1 million-plus contribution. Jonathan Choi has been a consistent donor to Michigan State University — Dr. Anil Jain’s home university during his adjunct tenure at Tsinghua University — since 2005 ($5 million).
University of California system
The University of California at San Diego is the outwardly apparent central hub for the Fudan-UC Center, a co-op of Shanghai’s Fudan University and the entire University of California system.176 Fudan University also enjoys a dual MBA program with MIT Sloan School of Management, hosted in Shanghai.177
UC San Diego also hosts the San Diego Supercomputer Center. Yifeng Cui, a Chinese researcher with past ties to Wuhan University for geological research, himself,178 is the founding Director of the High Performance GeoComputing Laboratory (HPGeoC) at SDSC.
San Diego Supercomputer Center’s “Voyager” is powered by Supermicro X12 Gaudi servers.179
University of California at Berkeley / Lawrence Berkeley National Lab
The U.S. House of Representatives released a report recently on the Shenzhen-Berkeley Institute, linking the Chinese manufacturing powerhouse city of Shenzhen to the University of California at Berkeley through Tsinghua University.180
This report could be in addendum to those same security risks outlined in the House report.
Berkeley is the main central office of the University of California system and the home of Lawrence Berkeley National Labs.
In 2017, the thirteenth batch of “Thousand Talents Program” youth projects were selected. According to official Chinese government documents from an official Guangzhou talent recruitment website, Berkeley had a member of the Thousand Talents Plan from Tsinghua University in 2017, one student of over 500 listed.181
In total, Berkeley had nine Thousand Talents in 2017 and Lawrence Berkeley National Laboratory had two. According to LinkedIn, one is still a postdoctoral researcher at the National Lab.182 The other professor’s page of the two at LBNL has since 2021 been removed, though the archived page reveals that the professor received his PhD from Hong Kong Polytechnic University (PolyU).183
Fortinet inked a deal with PolyU this very same year, 2017, to launch a first-of-its-kind cybersecurity training academy at the university.184
Also among these Thousand Talents scholars were students from the following schools and companies important to this report:
UC Davis — 5
UC Berkeley — 9
Stanford — 9
University of Washington — 4
University of Michigan — 11
UC Santa Barbara — 4
UCLA — 5
Michigan State — 1185
University of Southern California — 4
New York University — 4
UC San Diego — 4
Arizona State — 1
Carnegie Mellon University — 1
MIT — 14
Harvard — 18
Companies employing 2017 Thousand Talents — Juniper Networks, Intel, Apple, Amazon, Qualcomm, Lumentum, Illumina
Dozens of Thousand Talents scholars at National Institutes of Health and taxpayer supported National Labs
University of California at San Diego
The University of California at San Diego is home to the UC-Fudan Center and also the 21st Century China-U.S. Center.186 The Fudan-UC Center was established with now-former Fudan University Vice President Lin Shangli and eight other high-ranking Fudan University faculty members.187
Lin is a member of the Communist Party of China and is the President and Vice Chairman of the University Council of the Communist Party-founded188 Renmin University.189
The 21st Century China center directly links names like Chinese Communist Party and People’s Liberation Army to names like Jake Sullivan, Avril Haines, and David Ignatius, even if only through one event — the 2019 China Forum.190
Notably at the Forum was Ellen Nakashima who was awarded a Pulitzer for reporting on the NSA’s surveillance programs, notably following the mysterious and untimely death of Michael Hastings, who died in a strange, fiery, high-speed car crash in a residential area of Los Angeles in May of 2013.
Hastings’ strange, final purported email alleged that he was working on a story about the NSA. There is also still mystery surrounding that email and its actual origins.
Chinese alumni orgs prove complicity and collusion
The primary focus of this report revolves around Chinese infiltration of the United States’ semiconductor and cybersecurity supply lines, in both hardware, software and research, and the endless potential for hard-coding the same fundamental elements of the supposed-NSA’s Equation group of hacking tools — nearly indetectable until after an incursion into common pieces of commercial and military computing components.
This policy and process is certainly not exclusive to the entities addressed here. The People’s Republic of China is now widely known by those who follow the subject to establish alumni organizations in the United States to “promote Chinese language and culture,” like the P.R.C.’s Confucius Institutes.
Zhejiang University is a smoking gun of CIA complicity
Zhejiang University has been funneling the United States’ intellectual property and research to China for well over 20 years, whether illegally or not is immaterial to this end.
The American Zhu Kezhen Education Foundation (AZKEF) is a Zhejiang University-supported alumni organization and has been operating in the United States for decades. The Chinese government is alleged to keep some sort of direct line into these organizations, though the only outwardly verifiable instances of these are the limited cases that result in prosecution and subsequent conviction.
A common way for these alumni organizations to exchange money, talent, and sometimes trade and government secrets is through lectures, conferences, scholarships, grants, and employment opportunities.
In 2011 and 2012, AZKEF returned several then-U.S.-based alumni to Hangzhou for lectures at Zhejiang University which “check the boxes” for hotspots in this timeline:
Wayne State University
Michigan Secretary of State Jocelyn Benson took over the Wayne Law school after Committee of 100 (former) Chairman Frank Wu stepped down as Dean of the Wayne Law program; Her program began a series of visits to Beijing immediately upon this;
New York University
Jonathan H. Chao, professor at NYU, is a pivotal player to this story;
UC San Diego
The fulcrum and nerve center that coordinates between Fudan University and all 10 campuses of the University of California, which can then coordinate with Tsinghua University through the Tsinghua-Berkeley Shenzhen Institute. Both Fudan and Tsinghua have extensive ties to the business and management focus at both MIT and across all of Silicon Valley.

AZKEF offers several programs to its members, though several initiatives throughout the years outwardly and openly only served to benefit Zhejiang University.
One of these programs were the Distinguished Lectureship series which sent top American scholars directly to the main Hangzhou, Zhejiang province campus of Zhejiang University to give students there a lecture on any one or several of widely varying focuses.
Throughout the course of the Distinguished Lectureship Series, a clear pattern emerges and aligns with several key points of this report:
UCLA and UCSB had professors returning to Zhejiang University since 2004 despite the Zhejiang California Nanotechnology Institute;
UCSD and UC Berkeley sent plenty of professors to ZJU over the years;
University of Michigan was a recurring appearance, alongside a cameo from Michigan State University;
James M. Tiedje from Michigan State and Shu Chien from UC San Diego both visited Zhejiang University in 2015 while BGI’s Scientific Advisor Steve Hsu was Vice President of Research at Michigan State and while BGI was partnered with the Bill and Melinda Gates Foundation;
BGI is now on the United States’ Entities List of banned foreign entities
Stanford University sent a professor to Mainland China;
University of Illinois at Urbana-Champaign’s Harry Liebersohn made a trip in 2018 despite already enjoying full access to the UIUC-ZJU Institute;
Harvard and Columbia, like in the 2017 Thousand Talents roster, both had a pronounced presence with Zhejiang University’s U.S.-based alumni group.
In fact, these simple truths serve to further corroborate the underlying premise here: that the United States’ military-intelligence apparatus has spent decades and billions of dollars enriching themselves and their Chinese allies (including Taiwan and Hong Kong) at the expense of the American taxpayer and the taxpayers’ digital privacy.
Furthermore, the same apparatus also spent the better part of three decades posturing to scapegoat and betray the Chinese for a kinetic conflict over Taiwan to keep their injected, covert, prized spying technologies in what could easily be the entire world’s networking products a secret — for both sides.
Fudan, Tsinghua…and Friends
While Fudan University Education Development Fund isn’t necessarily an alumni group, they do serve a similar function as a pipeline for capital and other business transactions (or “donations”) between the Mainland China government and its U.S.-based operational assets.191192193194
In fact, between the years reporting 2013 and 2016, FUEDF gave a nonprofit apparently associated with Ming Hsieh’s Fulgent Therapeutics a total of nearly a million dollars ($953,867) in return for his generosity to the Mainland University.
According to ProPublica’s Nonprofit Explorer, Fudan University has three registered nonprofits for Fudan alumni groups: Los Angeles, and both Northern and Southern California.195
The Hsieh Family Foundation (Ming Hsieh’s 501(c)(3)-designated organization) contributed nearly $1.5 million to the Fudan University Education Development Fund in 2020, who also reported investments in Hong Kong that were linked directly to Mainland China, specifically Hangzhou and Zhejiang Province’s thriving autonomous vehicle technology market.
In fact, Ming Hsieh’s Fulgent Therapeutics Director Hanlin Gao is listed as the “General Manager” of Yishan (Zhejiang) Data Technology Co. in Hangzhou,196 but also as the Director of Fulgent’s Mainland China subsidiary.197
Hanlin Gao is also listed with Fulgent Therapeutics on several NIH awards.
According to past official U.S. policy, these types of conflicts of national security interests may not have even raised alarm until the repeated intrusions into American cyberspace that have been blamed on the Chinese for nearly two decades.
According to China Daily, the Center for American Studies at Fudan University was established by USAID in 1985.198
Since 1985, USAID and other U.S. taxpayer-funded programs have sent millions of dollars to these institutes being leveraged to flood out American tech workers, monitor American cyberspace, and siphon data from networks worldwide for training AI algorithms for “viral surveillance.”
This includes Tsinghua University between 2001 and 2008 to the tune of $12 million, but also another key player in this timeline: New York University.199200
Fudan University Institute of Higher Education
Fudan University, a renowned business-oriented university, and their Institute of Higher Education specifically reference on their website’s “About Us” section a collaboration with Tsinghua and Peking Universities201 — two of China’s top schools for business and law, respectively.
“Meanwhile, IHE conducts a large-scale, longitudinal Talent Research project in collaboration with other top universities such as Tsinghua University and Peking University. This research informs key policy strategies at the national level to identify and nurture high-achieving individuals, crucial for driving innovations and economic growth in China and fostering a more prosperous and equitable society worldwide.”
Tsinghua University and Friends
Tsinghua University’s alumni network in the U.S. is nothing short of remarkable. According to ProPublica’s Nonprofit Explorer, Tsinghua University maintains to some degree an assortment of twenty-three 501(c)(3) organizations carrying the unique name “Tsinghua.”202 Of these, twelve were in Southern California or Silicon Valley. Also represented are the Atlanta, Washington, D.C., Boston, Chicago, Seattle, Minneapolis, Houston, and Dallas-Ft. Worth metropolitan areas, as well as northern California and a larger “North America” association.
Tsinghua also maintains a dual degree program in computer science from as far back as 2012 with schools like Carnegie Mellon University203 in Pittsburgh, PA, who also leads CISA’s principal cybersecurity watchdog, CERT.
The now-widely known BRICS economic alliance was in fact launched formally from Tsinghua University in November of 2014,204 very soon followed by Tsinghua University, the University of Washington, and Microsoft launching the GIX Institute just outside Seattle, Washington in Bellevue.205
Now, the University of Washington and Microsoft exclude their familial roots with Tsinghua University entirely, even citing the year of first formal operation as its establishment, obscuring the correlation to Tsinghua.206
Tsinghua School of Economics and Management
The Tsinghua School of Economics and Management is Beijing’s apparent nerve center and melting pot for nearly every aspect of each of China’s successive Five-Year Plans. Tsinghua SEM singlehandedly provides an elite talent base to many of the financial and industrial levers of the world.
The compartmented but centrally managed School of Economics and Management, or SEM, is steered by its own Board of Advisors which is organized under the umbrella of the advisement of the university’s central, Communist Party leadership.
Tsinghua SEM also offers a joint MBA program with MIT Sloan School of Management207 in the same manner as Fudan University.208209 Readily apparent is the recycling of these interconnected universities’ alumni back into leadership positions of other “friendly” universities after graduation.
This recycling of talent internally is the concept underlying what some political pundits call “indoctrination,” but more importantly builds a closed system of familial trust for trained bad actors, or simply those who could be misguided by bosses who well may not have good intentions to exploit.
SEM Advisory Board — an American “Who’s Who”
The Tsinghua SEM Board of Advisors since 2022210211212213 has been packed with notable American names that have been labeled as oligarchs or corrupt by American politicians and media from both the political “left” and “right”.
Some of the recently consistent names on the Tsinghua SEM Advisory Board include but are not limited to:
Henry M. Paulson, Jr., Former U.S. Secretary of the Treasury/Former Chairman, CEO of Goldman Sachs
Elon Musk: CEO, SpaceX/xAI/The Boring Company
Jamie Dimon: CEO, JP Morgan
Jack Ma: Founder and CEO, Alibaba
Satya Nadella: CEO, Microsoft
Tim Cook: CEO, Apple
Jim Breyer: Founder/CEO, Breyer Capital
Ray Dalio: Founder/Member/CIO Mentor, Bridgewater Associates
Michael Dell: CEO/Chairman, Dell Technologies
Larry Fink: Chairman/CEO, Blackrock
David Rubenstein: Co-founder/Co-Chairman, The Carlyle Group
Stephen Schwarzman: Co-founder/CEO/Chairman, Blackstone
Masayoshi Son: CEO/Chairman, Softbank Group
Mark Zuckerberg: Founder/CEO, Meta
Due to the persistent saber rattling coupled with the current poor state of American national security being attributed to Chinese attacks, the most concerning names on the Tsinghua SEM Advisory Board aren’t American, but leaders of the Chinese Communist Party, the central government in Beijing, or leaders of the university, itself:
Wang Qishan (2024-2025): Former Vice President of China
Wang Xiqin (2022-2023): Deputy Secretary of the CPC Tsinghua University Committee, President of Tsinghua University
Zhu Rongji: Founding Dean of the School of Economics and Management at Tsinghua University/Former Premier, State Council, People’s Republic of China (1998-2003)
Li Luming (2023-2025): President of Tsinghua University
Qian Yingyi: Tsinghua University Chairman/Board of Trustees at Westlake University
Gu Binglin: Director of the Institute for Advanced Study at Tsinghua University/Former President of Tsinghua University
Zhao Chunjun: Former Dean (2001-2005) of the School of Economics and Management at Tsinghua University
Wang Dazhong: Former President of Tsinghua University
Friends of Tsinghua SEM
Names like Apple’s Tim Cook, former Kennedy Center Chairman David Rubenstein, and Jim Breyer of Breyer Capital appearing on the Tsinghua SEM Advisory Board is to be expected, as they all have appeared in Form 990 tax filings for the Tsinghua University-associated “Friends of Tsinghua SEM” 501(c)(3)-designated organization. Also noteworthy is Warren McFarlan, professor emeritus at Harvard Business School.
Tsinghua SEM North America Alumni Association
Shaozeng Guo, Weidong Ni, and Chunru Liu were listed as officers for the Tsinghua University School of Economics and Management Na Alumni Association, based in Burlingame, California for each of the reporting years 2015214 through 2018. In each of these filings, the organization also reported no transactions, no donations, no grants, no activity of any sort, even when filing for dissolution in 2018.
All but Liu were in attendance in New York for the inaugural ceremony with leadership of Tsinghua University and Chinese financial moguls. In an announcement posted to cgccusa.org, it clarified that Zhaozeng Guo was the Vice Chairman of China Fortune Land Development, Ltd., and Weidong Ni, the General Manager of Sino Environmental Engineering Development Co., Ltd. at the time.215
Transparency Is Needed
There are a painfully finite number of possibilities in regards to how these glaring conflicts between national security policy and national security narrative arose in this manner for so long; None of which being mutually exclusive to another, but very few of them paint a picturesque scene of the United States and China’s “backdoor” relationship.
Fortinet Zero-Day Exploit
Another security failure for Fortinet came right around the 2024 election when their entire system was subject to a dreaded “zero-day” vulnerability and being actively exploited.216217
2024 was yet another election year that held another in a continuing series of intrusive, highly critical cybersecurity breaches of a federal cybersecurity provider.
Deep-reaching, “in-network” arrests
At the end of January of this year, a Federal reserve advisor was arrested for selling trade secrets to China illegally.218 According to the reporting from Reuters:
The “…senior adviser in the Fed's division of international finance from 2010 until 2021, allegedly shared confidential information with Chinese co-conspirators. He is charged with conspiracy to commit economic espionage and with making false statements.”
He was alleged to be working with Shandong University, but the indictment read as though he was coordinating through Shanghai, the location of Fudan University (and many other things).
In that indictment, the D.O.J. even mentioned knowing the contents of encrypted messages.
Multiple Chinese nationals have been arrested in the recent weeks, months, and few years preceding this report, many alleged to have engaged in hacking activities, espionage, and the like.219220221
FPGAs, ASICs, integrated into everything
These easily concealable “backdoors” whose origins have been examined here are reprogrammable, thus able to be hidden or changed, and are known to be injected onto components that are vital for automobile sensors, GPS navigation, cybersecurity, email and communication servers, database platforms, and nearly any other advanced computing capabilities that the world has come to rely on for its most basic day-to-day operation.
There are at least three instances of emails, text messages, encrypted messages being accessed and made public under legally questionable if not outright criminal circumstances to point to as “red flags” that someone — or multiple someones — have the keys to the entire kingdom.
One of those instances just occurred again recently with the heads of U.S. intelligence and defense.
The only real question remaining after this report may be whether those keys are being used by the “bad guys” dressed as “good guys.”
Michael Hastings
There were a string of reports beginning around 2012 and continuing into 2014 about the NSA’s obsession with domestic backdoors, intrusive spying practices, use of malware, organized hacking programs, and several other alarming practices.
During this same time, portions of the intelligence community were taking repeated blows from the likes of Rolling Stone and Buzzfeed journalist Michael Hastings and so many others, but Hastings died in a freak car accident in a residential area of Los Angeles after 4am. There were swirling accusations of tampering with Hastings vehicle after the accident, specifically his cruise control and steering controls.
Days after the accident, a figure in some of Hastings work in Afghanistan, Sgt. Joe Biggs, came forward with an email he claimed to receive from Hastings in the hours before his death. Biggs claimed the email was blind carbon-copied to him, though the email he provided to media outlets had no “BCC” line in the image at all.
From there, Biggs was catapulted into relative fame among alternative media, and would go on to seed the infamous Comet Ping Pong gunman incident stemming from the Pizzagate line of “QAnon conspiracy theories.” Joe Biggs and Enrique Tarrio partnered in several endeavors beginning around 2018 and eventually went on to be instrumental in the chaos at the Capitol Building on January 6th, 2021.222223
Unmasking of Lt. Gen. (ret.) Michael Flynn
A second instance of unusually suspicious activity around supposedly private communications is former U.N. Ambassador Samantha Power’s 2016 unmasking of retired Lt. General Michael T. Flynn. Without a tip from specific people with specific clearance to not only know the existence of a 2013 FISA-netted communication between Flynn and a Russian national, but to already know whose name was redacted at all points to an insider collusion that chills the very legitimacy of American democracy.
There was no adjudication to collect this communication on the Senate-confirmed Director of Defense Intelligence Agency — even if incidentally collected in the course of routine foreign surveillance; There was no adjudication to disclose the record to any government official; There was no pending judicial process that required its use until the infamous Steele Dossier, therefore Power’s knowing of its existence was impossible without insider — illegal — help.224
Pete Hegseth, Mike Waltz Signal messages leak
The third, most recent, and by far the most egregious of these examples is the leak of “war plans” that were supposedly contained within private Signal messages that allegedly included a so-called “journalist” at The Atlantic.
Alex Wong, a deputy to current National Security Advisor Mike Waltz (ironically the same post from which Flynn was targeted for removal by external forces), is from the belly of the machine laid out above in this report, UC San Diego’s 21st Century China Center.225
This raises immense suspicion about the sourcing of those encrypted messages, as the only entity with the encryption key would be in those messages. This makes it imperative that the journalist post the entirety of his collection — WITH metadata.
If this is evidence that critical systems are already backdoored by people on the “inside,” then what could that say about other critical systems we as Americans rely on to run our society?
Digital Voting
A common reprise from skeptics of claims of widespread election fraud and vote manipulation by tabulation machines, and even allegations of voter roll tampering could be easily explained with direct evidence that those systems’ firmware had been compromise with pieces of executable code lying dormant and awaiting reassembly from some other activating signal.
To date, there has been no clear and convincing evidence introduced to a legal forum to indicate this has been the case at any point in time. However, Dominion’s notorious Democracy Suite voting platform runs on any combination of hardware, but provides specifications for Supermicro motherboards with multiple systems utilizing FPGAs that require specific firmware for testing.
Konnech
Even further evidence of the Intelligence Community’s complicity and subsequent coverup is found in the election scandal surrounding a sleepy Michigan company called Konnech.
Ironically, Eugene Yu himself was a member and an officer of the American Zhu Kezhen Education Foundation (AZKEF)226 the very year that they sent the now-Fortinet Founders Chair Professor Yi Cui’s PhD. advisor Charles Lieber to Zhejiang University, also the very year Yi Cui finished the aforementioned PhD requisites.
Also coincidental, Lionel Ni was a Michigan State professor who apparently licensed his product, the EMIP-1, to Konnech around 2001-2002; Ni’s products were developed in part from work performed for an elusive NSF Microelectronic Systems Architecture Program, funded by the U.S. federal government.
As the Director of that program, Dr. Ni was able to presumably elaborate and expound upon the very technology he was tasked to create all the way back in 1992 at Michigan State University, which made cloud computing and the “backdoors” a viable reality.227
Lionel Ni’s PhD student, Xipeng Xiao, was also a member of the AZKEF alumni organization, and is now in executive leadership for Huawei in Germany.228
Konnech’s Eugene Yu, for another report at another time, was obviously involved with Fudan University Board member and MSU donor, but also Chinese Academy of Sciences’ President’s financial advisor Jonathan KS Choi, a Hong Kong billionaire, and engaged in a sort of “interplay” with Michigan State’s K-12 Chinese School funded by Choi.
Covid, Genetics, and Social Profiling
These universities in question within this report, in the very same computer science and engineering programs, often engage in cross-discipline research focused on leveraging advanced analytics toward understanding many other, concerning academic focal points when viewed in hindsight of the last fifteen years: manipulation tactics in media and online, radical extremism, race issues, socioeconomic profiling, social engineering, social deception, the impacts of AI-generated content, etc., which are so diverse, comprehensive, focused, and widespread, they would be best suited for another lengthy and detailed report, entirely; However, these programs themselves would have astronomical impacts on the discussion around civil liberties, truthful information in media, and the very premise of “free will,” if examined closely and critically at those principle’s dissemination throughout American society.
Major political ramifications already realized
It’s well known the Gates Foundation’s influence in American politics for the better part of two decades at this point, but with the advent of the Arabella Advisors power moves in political networking, the Gates Foundations’ health initiatives also coincided neatly with many of the technologies (AI, biometrics, microsystems engineering) being developed at the same American universities who were centers of political and economic power and influence.
New Jersey Drones
There is other potential evidence of these same types of networks possibly at play in America, found in the recent drone sightings nearby military installations nationwide. A fortunate discovery of a large downed drone owned by a company called Amogy,229 a company originating and relying heavily on talent from MIT Sloan School of Management,230231232 who as previously discussed, is closely connected to both Tsinghua and Fudan universities.
American Campus Unrest
Whether the financial apparatus behind Silicon Valley’s talent pool is the same apparatus behind the extended peaks in unrest at American universities remains to be seen, though it is at least noteworthy that the same American universities named here are at times the same universities being pummeled with violence and hate on a semi-regular basis for nearly a decade.
Aviation
Ever since exactly the time just before 9/11, there have been ways to remotely access “bugs” already implanted into systems, the methods here are moot. This opens the possibility to reprogrammed flight computers, altered GPS systems, remote navigation, and many more very troubling possibilities, layered on top of already existing hardware, mechanical, and maintenance failures of America’s top airlines. The consequences of a disaster, or a cascading series of disasters stemming from of an unsecured aviation infrastructure are incalculable.233
In light of some sort of complicity of the United States intelligence complex toward the Communist Party of China, taking another look at the Department of Justice arresting three Chinese nationals attempting to do precisely something of this sort raises enormous questions into how long this method has been leveraged.
Since 2015, cyber experts have noticed and analyzed the similarities between the suspected NSA Equation Group and the APT-named hacking groups worldwide; Writers even highlighted the EQUATION Group’s premonition into complex exploits and vulnerabilities no other formidable groups had identified as of 2015, when this report begins its most intensive focus.234
This is alarming knowing that most confidential information — anyone’s confidential information, about anything — is likely already completely compromised and/or possessed by the Communist Chinese government and/or the United States Intelligence Community.
Fortinet has already sold Chinese-made equipment to the U.S. Military and got away with effectively a slap on the wrist of a half-million dollars on penalties.235
If the Intelligence Community possesses or has been accessing private information — like emails — from private companies without any sort of process, or without first securing judicial warrants, then there are more pressing matters at hand than broadcasting outrage over the D.O.G.E. group’s access to logs of taxpayer-backed transactions.
In Closing
The Chinese Communist Party unabashedly has been pressing and extracting the United States tech industry and military-intelligence base for capital investments into their universities who then perform research to be absorbed into the People’s Liberation Army’s tech portfolio. Those researchers then are granted scholarships, often from the United States government, but even more often from Chinese government-backed, U.S.-based talent and alumni groups. Those scholars then either 1) Return to China with all of their research and American-funded knowledge to reintegrate into the Chinese system; 2) Become career scholars in the U.S., often furthering the same schools’ connections back to China; 3) Move directly into the defense industry at National Laboratories or with contractors; or 4) Move into Silicon Valley and the commercial tech industry.
This problem is not a relic of history, has never been addressed, and somehow still persists today with reports of Supermicro, NVIDIA, and several other computer hardware manufacturers and distributors somehow sneakily getting their products to China, despite recent tightening of export controls around that specific industry.236
Clearly the Chinese are aiming to maintain their grip on artificial intelligence — they have been “backdooring” systems for over a decade for a specific, undeclared reason.
In fact, just in 2019, Fortinet paid a mere $540,000 settlement to the U.S. government for selling it Chinese hardware for around seven years between January 2009 and the fall of 2016.237 There are a limited number of creative applications for illegally acquiring these specific products while also possessing knowledge of the “backdoor” systems, and NVIDIA has publicly raised its own questions on the matter.238
All of these potential outcomes always come with the sidenote that Chinese-born, U.S.-employed residents and even naturalized citizens stay in touch via private portals like CNBrief, developed by Eugene Yu’s Konnech for the Confucius Institutes in 2013.
The entire nation’s cyber infrastructure has always been one file download away from “Zero-Day.”
With American taxpayer money purchasing the services and products from these companies who are led by American intelligence assets, partner with American intelligence assets’ universities, or built by American intelligence assets off the fruits of CCP and PLA researchers who develop and work in these roles to further the Communist Chinese agenda, this deserves swift, decisive action in legislative bodies nationwide — not ONLY in the Congress.
The interconnection is so deep and ripe for crime, there is no direct action needed to take heed. This is a threat to national security, even if these mechanisms exist for our own intelligence services. Nevertheless, if this is the case, this also raises enormous concerns toward civil liberties and the Constitutional right to privacy.
Staying permanently inseparable from the Chinese Communist Party is a lethal liability to Americans who must understand that the price of which is their very livelihoods, or God forbid, their lives.
Footnotes:
Lucian Constantin, “Despite patches, Supermicro’s IPMI firmware far from secure, researchers say” (InfoWorld, 7 Nov 2013; web link: https://www.infoworld.com/article/2182416/despite-patches-supermicro-s-ipmi-firmware-far-from-secure-researchers-say.html)
CARI, “CARISIRT: Yet Another BMC Vulnerability (And some added extras),” (CARI.net; 19 Jun 2014; archived: https://web.archive.org/web/20140622122837/http://blog.cari.net/carisirt-yet-another-bmc-vulnerability-and-some-added-extras/)
Dan Goodin,”At least 32,000 servers broadcast admin passwords in the clear, advisory warns” (ARS Technica, 19 Jun 2014; web link: https://arstechnica.com/information-technology/2014/06/at-least-32000-servers-broadcast-admin-passwords-in-the-clear-advisory-warns/)
Jordan Robertson, Michael Riley, “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies” (Bloomberg Businessweek, 4 Oct 2018) (archived: https://web.archive.org/web/20181026081155/https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies)
Jordan Robertson, Michael Riley, “The Big Hack: Statements From Amazon, Apple, Supermicro, and the Chinese Government” (Bloomberg, 4 Oct 2018; archived: https://web.archive.org/web/20181031000611/https://www.bloomberg.com/news/articles/2018-10-04/the-big-hack-amazon-apple-supermicro-and-beijing-respond)
Amir Efrati, “Apple Severed Ties with Server Supplier After Security Concern” (The Information, 23 Feb 2017; web link: https://www.theinformation.com/articles/apple-severed-ties-with-server-supplier-after-security-concern)
Charles Liang, Supermicro, “Testing Finds No Malicious Hardware on Supermicro Motherboards…Letter From The CEO” (Supermicro, 11 Dec 2018; archived: https://web.archive.org/web/20181211165126/https://www.supermicro.com/en/news/CEO-3rdPartySecurity-Update)
Pierluigi Paganini, “Flaw in update process for BMCs in Supermicro servers allows to deliver persistent malware or brick the server” (Security Affairs, 7 Sep 2018; archived: https://web.archive.org/web/20240413153332/https://securityaffairs.com/75999/hacking/flaw-supermicro-servers.html)
Eclypsium, Firmware Vulnerabilities in Supermicro Systems (Eclypsium.com, 7 Jun 2018; link: https://eclypsium.com/research/firmware-vulnerabilities-in-supermicro-systems/)
Serve The Home, “Investigating Implausible Bloomberg Supermicro Stories” (ServeTheHome.com, 22 Oct 2018; archived: https://web.archive.org/web/20181022210314/https://www.servethehome.com/investigating-implausible-bloomberg-supermicro-stories/)
Lehar Maan, Liana B. Baker,“Intel to buy Altera for $16.7 billion in its biggest deal ever", (Reuters, 1 Jun 2015; archived: https://web.archive.org/web/20181124212755/https://www.reuters.com/article/us-altera-m-a-intel/intel-to-buy-altera-for-16-7-billion-in-its-biggest-deal-ever-idUSKBN0OH2E020150601/)
Super Micro Computer, Inc.,“BMC Unique Password Security Feature, November 2019” (Supermicro Customer Announcement, 27 Nov 2019; archived: https://web.archive.org/web/20191127092629/https://www.supermicro.com/en/support/BMC_Unique_Password)
Jordan Robertson, Michael Riley, “The Long Hack: How China Exploited a U.S. Tech Supplier” (Bloomberg, 12 Feb 2021; archived: https://web.archive.org/web/20210212112437/https://www.bloomberg.com/features/2021-supermicro/)
Binarly Research Team, Binarly REsearch Uncovers Major Vulnerabilities in Supermicro BMCs (binarly.com, 3 Oct 2023; archived: https://web.archive.org/web/20240417114115/https://www.binarly.io/blog/binarly-research-uncovers-major-vulnerabilities-in-supermicro-bmcs)
Jonathan Weil, Justice Department Probes Server Maker Super Micro Computer (New York Times, 26 Sep 2024; archived: https://web.archive.org/web/20240926151139/https://www.wsj.com/tech/justice-department-probes-server-maker-super-micro-computer-2ca6a4d3)
Micah Lee, Henrik Moltke, “Everybody Does It: The Messy Truth About Infiltrating Computer Supply Chains” (The Intercept, 24 Jan 2019; archived: https://web.archive.org/web/20190124201626/https://theintercept.com/2019/01/24/computer-supply-chain-attacks/)
Kaspersky Lab, “Equation Group: The Crown Creator of Cyber-Espionage” (Kaspsersky Lab, 17 Feb 2015; archived: https://www.kaspersky.com/about/press-releases/equation-group-the-crown-creator-of-cyber-espionage)
Kaspersky Lab, EQUATION GROUP: QUESTIONS AND ANSWERS (Kaspersky Lab, February 2015; archived: https://web.archive.org/web/20190508170111/https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/08064459/Equation_group_questions_and_answers.pdf)
BUREAU OF INDUSTRY AND SECURITY, Office of Congressional and Public Affairs, “Commerce Department Prohibits Russian Kaspersky Software for U.S. Customers” (20 Jun 2024; archived: https://web.archive.org/web/20240620212150/https://www.bis.gov/sites/default/files/press-release-uploads/2024-06/KL-press_release-CLEAN.pdf)
Dan Goodin, “How “omnipotent” hackers tied to NSA hid for 14 years—and were found at last” (ARS Technica, 16 Feb 2015; archived: https://web.archive.org/web/20170920030240/https://arstechnica.com/information-technology/2015/02/how-omnipotent-hackers-tied-to-the-nsa-hid-for-14-years-and-were-found-at-last/)
Kaspersky Lab, EQUATION GROUP: QUESTIONS AND ANSWERS (Kaspersky Lab, February 2015; archived: https://web.archive.org/web/20190508170111/https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/08064459/Equation_group_questions_and_answers.pdf)
CNN, “Hackers got into Davos system” (CNN.com, 4 Feb 2001; archived: https://web.archive.org/web/20010622003333/https://edition.cnn.com/2001/WORLD/europe/02/04/davos.hackers/index.html)
Various authors, “Code Red (computer worm)” (Wikipedia: https://en.wikipedia.org/wiki/Code_Red_(computer_worm))
Various authors, “Nimda” (Wikipedia: https://en.wikipedia.org/wiki/Nimda)
CERT Division, Carnegie Mellon University, 2001 CERT Advisories (Carnegie Mellon University Software Engineering Institute, 2017; https://web.archive.org/web/20230923225001/https://insights.sei.cmu.edu/documents/508/2001_019_001_496192.pdf), 129
Trevor Timm, “Building backdoors into encryption isn't only bad for China, Mr President” (The Guardian, 4 Mar 2015; archived: https://web.archive.org/web/20150311230402/https://www.theguardian.com/commentisfree/2015/mar/04/backdoors-encryption-china-apple-google-nsa)
Sergei Skorobogatov, Christopher Woods, “Breakthrough silicon scanning discovers backdoor in military chip” (University of Cambridge, Quo Vadis Labs; 28 Sep 2012 archived: https://web.archive.org/web/20120928053416/https://www.cl.cam.ac.uk/~sps32/ches2012-backdoor.pdf)
Robert Graham, “Bogus story: no Chinese backdoor in military chip” (Errata Security, 28 May 2012; archived: https://web.archive.org/web/20131006004426/https://blog.erratasec.com/2012/05/bogus-story-no-chinese-backdoor-in.html)
Zacks Investment Research, “Microchip (MCHP) Completes Microsemi Acquisition for $10.3B” (NASDAQ.com, 30 May 2018; archived: https://web.archive.org/web/20220626120206/https://www.nasdaq.com/articles/microchip-mchp-completes-microsemi-acquisition-for-%2410.3b-2018-05-30)
Arizona State University, Microelectronics map (archived 2 May 2024: https://web.archive.org/web/20240502215256/https://news.asu.edu/sites/default/files/Microelectronics-map.pdf)
Microchip Technology, Inc., MicroSOLUTIONS (Microchip Technology, Inc. April 2008 Newsletter; archived: https://web.archive.org/web/20250327040312/https://ww1.microchip.com/downloads/en/Market_Communication/APRIL%202008%20microSOLUTIONS.pdf), 18.
Arizona State University, COLLEGE MARSHALS FALL 2019 (Arizona State University Commencement and Convocation Program, Fall 2019, 255; archived: https://web.archive.org/web/20211120041636/https://graduation.asu.edu/sites/default/files/asu_fall_2019_allpageconvbookwebfinal_11.9.2020.pdf)
Electronic Design Innovation Conference 2013, Conference Guide (Electronic Design Innovation Conference 2013, Beijing International Convention Center, Beijing, China, 12-14 Mar 2013; archived: https://web.archive.org/web/20170829004641/http://www.microwavejournal.com/ext/resources/EDICON/2013/Guides/EDICON-CONFERENCE-PROGRAM-WEB.pdf)
Electronic Design, June 2016; (archived: https://web.archive.org/web/20240807123549/https://base.imgix.net/files/base/ebm/electronicdesign/document/2022/10/ED_2016_06_DE.6356a0eed71e9.pdf)
NETWORK-1 TECHNOLOGIES, INC. v. FORTINET, INC., 1:22-cv-01319-MN; 21 Mar 2023, archived: https://web.archive.org/web/20250327192114/https://insight.rpxcorp.com/litigation_documents/15156097)
University of Michigan, Crossbar ReRAM Technology Enabling AI (EECS — A YEAR IN REVIEW, 2018, 37; archived: https://web.archive.org/web/20230325223212/https://ece.engin.umich.edu/wp-content/uploads/sites/4/2019/08/EECSNews18.pdf)
NCURA Magazine, VOLUME XLVII, NO. 4, August 2015; (archived: https://web.archive.org/web/20240730133226/https://www.research.ucf.edu/documents/PDF/com_August2015_NCURA_Magazine.pdf)
Intel Corporation, Intel Officially Opens Vietnam Assembly and Test Facility (Intel News Release, 29 Oct 2010; archived: https://web.archive.org/web/20160416221626/https://www.intel.co.jp/content/dam/www/public/apac/xa/en/asset/world-economic-forum/pdf/Investing%20in%20asean%20region/article%204/VNAT%20Opening%20press%20release%20102910%20Final.pdf)
Formerly Altera d.b.a. Intel Corporation, PRODUCT DISCONTINUANCE NOTIFICATION PDN1810 (Intel Corporation customer announcement, 1 Feb 2019; archived: https://web.archive.org/web/20250326055238/https://www.altera.com/content/dam/altera-www/global/en_us/pdfs/literature/pcn/pdn1810.pdf)
Super Micro Computer, Inc., “Supermicro Expands Intelligent Edge Product Portfolio to address emerging AI and 5G Technologies” (Supermicro Press Release, 25 Feb 2019; archived from Supermicro.org.cn (China): https://web.archive.org/web/20250326044312/https://www.supermicro.org.cn/newsroom/pressreleases/2019/press190225_Edge_Systems_for_AI_and_5G.cfm)
Intel Coporation, Cyclone® FPGA and Cyclone® V SoC Devices, (All Cyclone® FPGA Generations, Intel.com; archived: https://web.archive.org/web/20250326054556/https://www.intel.com/content/www/us/en/products/details/fpga/cyclone.html)
Intel Corporation, Intel Launches Altera, Its New Standalone FPGA Company (Intel.com, 29 Feb 2024; archived: https://web.archive.org/web/20250216210755/https://newsroom.intel.com/artificial-intelligence/intel-launches-altera-standalone-fpga-operation)
Fortinet and Intel: Innovating with Visionary Security Technologies and Solutions (Fortinet-Intel white paper, 6 Feb 2019; archived: https://web.archive.org/web/20200930095257/https://www.fortinet.com/content/dam/fortinet/assets/alliances/2019/sb-fortinet-alliances-intel.pdf)
Fortinet and Vyatta Deployment Guide, (archived: https://web.archive.org/web/20150512002614/http://www.brocade.com/products/all/software-defined-networking/brocade-vyatta-controller/index.page)
FortiDDoS and FortiDDoS CM 5.3.2 Release Notes (Fortinet, 15 May 2023; archived: https://web.archive.org/web/20250411053541/https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/777cba8c-f410-11ed-8e6d-fa163e15d75b/Release_notes_PDF.pdf)
Marketwire, Fortinet(R) Unveils Second Generation FortiASIC-SoC2 (chipestimate.com, 12 October 2012; archived: https://web.archive.org/web/20250411013533/https://www.chipestimate.com/FortinetR-Unveils-Second-Generation-FortiASIC-SoC2/Intel/news/18683)
HOWTO - Monitoring FortiSIEM Hardware Appliances (Fortinet, https://community.fortinet.com/tpykb84852/attachments/tpykb84852/TKB28/445/1/HOWTO%20Monitoring%20FortiSIEM%20Hardware%20Appliances.pdf
CVE.org results for fortinet authentication (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet+authentication)
IETF 88 Working Group Roster (IETF, 2013; archived: https://web.archive.org/web/20250226224701/https://www.ietf.org/proceedings/88/bluesheets/bluesheets-88-dhc-01.pdf)
CVE.org results for fortinet firmware (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet+firmware)
CVE.org results for fortinet inject (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet+inject)
CVE.org results for fortinet administrator (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet+administrator)
CVE.org results for fortinet credentials (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet+credentials
CVE.org results for fortinet (link: https://www.cve.org/CVERecord/SearchResults?query=fortinet)
Fortinet, Inc., Former Governor, U.S. Commerce Secretary, and U.S. Ambassador, Gary Locke, joins Fortinet Board of Directors (Press Release, 28 Sep 2015; archived: https://web.archive.org/web/20200924123544/https://www.fortinet.com/br/corporate/about-us/newsroom/press-releases/2015/former-governor-us-commerce-secretary-gary-locke-joins)
Amol Sarwate, Equation Group Hack: Cisco ASA and FortiGate Vulnerabilities (Qualys Communities, 18 Aug 2016; archived: https://web.archive.org/web/20210804144656/https://blog.qualys.com/vulnerabilities-threat-research/2016/08/18/equation-group-hack-cisco-asa-and-fortigate-vulnerabilities)
Darren Pauli, Equation Group exploit hits newer Cisco ASA, Juniper Netscreen (theregister.com, 24 Aug 2016; archived: https://www.theregister.com/2016/08/24/equation_group_exploit_expanded_to_target_cisco_924_asa_boxes/)
Martyn Warwick, Have the Chinese/Russians had backdoor access to Juniper kit for the past three years? (telecomtv.com, 22 Dec 2015; https://www.telecomtv.com/content/security/have-the-chinese-russians-had-backdoor-access-to-juniper-kit-for-the-past-three-years-13164/)
Tom Taulli, “The Man Who Made Two Multibillion-Dollar Companies” (Forbes, 6 Feb 2012; archived: https://web.archive.org/web/20120207065839/https://www.forbes.com/sites/tomtaulli/2012/02/06/a-man-who-made-two-multibillion-dollar-companies/)
Michael Xie | Board of Directors (investor.fortinet.com, 14 Jan 2021; archived: https://web.archive.org/web/20210114170541/https://investor.fortinet.com/board-directors/michael-xie)
Zacks Equity Research, “New Data Breach Puts 3 Cyber Security Stocks in Focus - Analyst Blog” (Yahoo! Finance, 8 Jun 2015; archived: https://web.archive.org/web/20150625044344/https://finance.yahoo.com/news/data-breach-puts-3-cyber-171805207.html)
Globe Newswire, Fortinet Appoints Phil Quade as Chief Information Security Officer (Fortinet Investor Relations, 10 Jan 2017; archived: https://web.archive.org/web/20240619114129/https://investor.fortinet.com/static-files/16d515cb-75cc-4074-90d5-d9db81aa6004)
Globe Newswire, Fortinet Launches Fortinet Federal, Inc. and its Board of Directors (Fortinet Investor Relations, 15 May 2017; archived: https://web.archive.org/web/20250328042634/https://investor.fortinet.com/static-files/639c5e59-b10a-4784-9a5b-fbfaf5aad51f)
Meltdown and Spectre Side-Channel Vulnerability Guidance (CISA, 4 Jan 2018; archived: https://web.archive.org/web/20230315180105/https://www.cisa.gov/news-events/alerts/2018/01/04/meltdown-and-spectre-side-channel-vulnerability-guidance)
Lucian Armasu, “State-Sponsored Chinese Group Hacks Enterprise VPN Servers” (Tom’s Hardware, 6 Sep 2019; archived: https://web.archive.org/web/20200807095345/https://www.tomshardware.com/news/apt25-hacks-enterprise-vpn-servers-security,40342.html)
U.S. Senator Charles E. Grassley, Letter to Ken Xie (United States Senate Committee on the Judiciary, 15 January 2025; https://www.grassley.senate.gov/imo/media/doc/grassley_to_fortinet_-_salt_typhoon_hack.pdf)
Written Testimony of Rob Rashotte (U.S. House Committee on Homeland Security Hearing on “Preparing the Pipeline: Examining the State of America’s Cyber Workforce”, 5 Feb 2025; archived: https://web.archive.org/web/20250214194400/https://homeland.house.gov/wp-content/uploads/2025/02/2025-02-05-HRG-Testimony.pdf)
Michael M. Crow, Curriculum Vitae (Arizona State University 2025 CV, 1; archived: https://web.archive.org/web/20250329014721/https://president.asu.edu/sites/default/files/2025-01/Crow_Curriculum_Vitae_2025_01-01_0.pdf)
Michael M. Crow, Curriculum Vitae (Arizona State University 2025 CV, 2; archived: https://web.archive.org/web/20250329014721/https://president.asu.edu/sites/default/files/2025-01/Crow_Curriculum_Vitae_2025_01-01_0.pdf)
Various Authors, Stephen Hsu (Wikipedia, https://en.wikipedia.org/wiki/Stephen_Hsu)
Kirsten Searer, ASU's Crow partners with CIA on research projects (30 March 2003; archived: https://web.archive.org/web/20190914022050/https://www.eastvalleytribune.com/news/asu-s-crow-partners-with-cia-on-research-projects/article_85f402f5-21ed-5973-8bd0-e3e3f721c88a.html)
Declan McCullagh, SafeWeb's Holes Contradict Claims (Wired, 12 Feb 2002, archived: https://web.archive.org/web/20180613071837/https://www.wired.com/2002/02/safewebs-holes-contradict-claims/)
Nathan Walker (“Gus Quixote”), Stephen Hsu (Theory No More, Part Nine: Merry Christmas, 25 Dec 2024; archived: https://web.archive.org/web/20241225181419/https://gusquixote.substack.com/p/theory-no-more-part-nine-merry-christmas; selection: https://gusquixote.substack.com/i/153589501/stephen-hsu)
Webpage: Confucius Institute at Arizona State University (archived: https://web.archive.org/web/20090803051728/http://confuciusinstitute.asu.edu/)
Parallel Systems and Computing Laboratory (PSCLab) (asu.edu; archived: https://web.archive.org/web/20240911101337/https://ren-fengbo.lab.asu.edu/content/altera)
innercirclepost, Open Graduate Research Assistant (GRA) position (ASU innercircle, 31 August 2015; archived: https://web.archive.org/web/20150901150026/https://innercircle.engineering.asu.edu/2015/08/31/open-graduate-research-assistant-gra-position/)
Fengbo Ren, Curriculum Vitae, 1 (Arizona State University, 26 May 2021; archived: https://web.archive.org/web/20220814144447/https://ren-fengbo.lab.asu.edu/sites/default/files/group_member_cv/cv_fengbo_ren_asu_0.pdf)
Hong Kong University of Science and Technology, Genesis (HKUST Newsletter, Fall Semester 2006-07; archived: https://web.archive.org/web/20250329044733/https://archives.hkust.edu.hk/server/api/core/bitstreams/0081178b-3ba8-4aed-8e67-82115de751f2/content)
Chinese Talent Programs (COUNTER INTELLIGENCE STRATEGIC PARTNERSHIP INTELLIGENCE NOTE (SPIN), September 2015; archived: https://web.archive.org/web/20171127054053/https://info.publicintelligence.net/FBI-ChineseTalentPrograms.pdf)
Bill Priestap, “China’s Non-Traditional Espionage Against the United States: The Threat and Potential Policy Responses” (Statement Before the Senate Judiciary Committee, 12 Dec 2018; archived: https://web.archive.org/web/20181228153051/https://www.fbi.gov/news/testimony/chinas-non-traditional-espionage-against-the-united-states)
香港科技园欲成立大中华半导体IP交易平台 (Hong Kong Science and Technology Park wants to set up a large Chinese semiconductor IP trading platform, 27 Nov 2005; archived: https://web.archive.org/web/20250329055041/http://www.cnhubei.com/200511/ca934711.htm)
Carol Morello, Pompeo declares Hong Kong no longer autonomous from China (The Washington Post, 27 May 2020; archived: https://web.archive.org/web/20200528145951/https://www.washingtonpost.com/national-security/pompeo-declares-hong-kong-no-longer-autonomous-from-china/2020/05/27/2773096c-a036-11ea-9d96-c3f7c755fd6e_story.html)
California NanoSystems Institute (CNSI) (UCLA, archived: https://web.archive.org/web/20240707221833/https://ctsi.ucla.edu/california-nanosystems-institute-cnsi)
Zhejiang California International NanoSystems Institute (ZCNI) (zcni.zju.edu.cn, 9 Sep 2013; archived: https://web.archive.org/web/20130909101420/http://www.zcni.zju.edu.cn/en/main_en.html)
浙江大学(第2期)单细胞组学专题研习班通知 (Zhejiang University, 20 July 2021; archived: https://web.archive.org/web/20230329093406/http://www.zcni.zju.edu.cn/attachments/2021-07/07-1626924415-18514.pdf)
浙江大学“基因组科学”(总60期)研习班通知 (Zhejiang University, 6 March 2021; archived: https://web.archive.org/web/20210506161740/http://www.zcni.zju.edu.cn/attachments/2021-03/07-1614912012-17819.pdf)
浙江大学第7期“蛋白质组学”专题研习班邀请函 (Zhejiang University, 2 January 2020; archived: https://web.archive.org/web/20240704022645/http://www.zcni.zju.edu.cn/attachments/2020-01/07-1577930103-16110.pdf)
浙江大学第5期“基因编辑”技术专题研习班邀请函 (Zhejiang University, 16 April 2019; archived: https://web.archive.org/web/20230329111053/http://www.zcni.zju.edu.cn/attachments/2019-04/07-1555466381-15579.pdf)
浙江大学“转录调控数据分析及R语言作图”(第4期) 研习班邀请函i (Zhejiang University, 10 April 2018; archived: https://web.archive.org/web/20230329093822/http://www.zcni.zju.edu.cn/attachments/2018-04/07-1524904805-14299.pdf)
ZJU delegation strengthen ties with top North American institutions (zju.edu.cn, 27 October 2023; archived: https://www.zju.edu.cn/english/2023/1109/c65150a2825095/page.htm)
International Technology Transfer Center (China Ministry of Science and Technology, 30 June 2009; archived: https://web.archive.org/web/20250403020818/https://en.most.gov.cn/newsletters/2009/200906/t20090630_71547.htm)
Center Introduction/ About Us (hic.zju.edu.cn, archived: https://web.archive.org/web/20240816180738/https://hic.zju.edu.cn/zxjj/list.htm)
ZJUI Overview (Zhejiang University, “About” page, link: https://zjui.intl.zju.edu.cn/en/college)
Advanced Semiconductor Research Institute (hic.zju.edu.cn, 2 Apr 2021; archived: https://web.archive.org/web/20241211083452/https://hic.zju.edu.cn/hicenglish/2021/0402/c56823a2275375/page.htm)
Advanced Semiconductor Research Institute (hic.zju.edu.cn, 05 July 2024; archived: https://web.archive.org/web/20250330022038/https://hic.zju.edu.cn/hicenglish/2024/0705/c82820a2949963/page.htm)
Industry Partnership (hic.zju.edu.cn, archived: https://web.archive.org/web/20250330023201/https://hic.zju.edu.cn/hicenglish/wollaborate/list.htm)
MOE Civil-Military Innovative Research Center for Micro-Satellite and Constellation (esaa.zju.edu.cn, archived 22 July 2019: https://web.archive.org/web/20190722024607/http://esaa.zju.edu.cn/2018/1011/c21715a874498/page.htm)
Jeffrey Stoff, Glenn Tiffert, Under the Radar: National Security Risk in US-China Scientific Collaboration (Hoover Institution, 2021; archived: https://web.archive.org/web/20210615003757/https://www.hoover.org/sites/default/files/research/docs/tiffert_globalengagement_ch1-08181.pdf)
Super Micro Computer Annual Report, 2019 (https://web.archive.org/web/20250330052346/https://stocklight.com/stocks/us/nasdaq-smci/super-micro-computer/annual-reports/nasdaq-smci-2019-10K-191296852.pdf)
LinkedIn: https://www.linkedin.com/in/xuzhou/
Xidian University 西安电子科技大学 (unitracker.aspi.org.au, archived: https://web.archive.org/web/20250313010051/https://unitracker.aspi.org.au/universities/xidian-university/)
Professional Catalog of Graduate Enrollment in the Electrical Institute (Xidian University, archived: https://web.archive.org/web/20190821003946/http://see.xidian.edu.cn/html/page/199.html)
The Guardian, “US embassy cables: China uses access to Microsoft source code to help plot cyber warfare, US fears” (The Guaridan, 4 December 2010; archived: https://www.theguardian.com/world/us-embassy-cables-documents/214462?_ga=2.97776351.1319451064.1567722102-1036413872.1567722102)
Chenming Hu, Curriculum Vitae (UC Berkeley, archived: https://web.archive.org/web/20250331023848/https://www.chu.berkeley.edu/cv/)
Taiwan Semiconductor Manufacturing Company, TSMC CTO Dr. Chenming Hu Returns to Academia (TSMC, 11 June 2004; archived: https://web.archive.org/web/20250408020345/https://pr.tsmc.com/english/news/1300)
Various Authors, Chinese Academy of Sciences (Wikipedia, https://en.wikipedia.org//wiki/Chinese_Academy_of_Sciences)
College of Computing, Data Science, and Society (CDSS) Advisory Board https://web.archive.org/web/20250410110936/https://cdss.berkeley.edu/pehong-chen-phd-88)
CASPA- About (CASPA.com, 2000; archived: https://web.archive.org/web/20000407202146/http://www.caspa.com:80/about.htm)
Chinese American Semiconductor Professional Association Austin Chapter, “Who we are?” (CASPA.com, 2002; archived: https://web.archive.org/web/20020520102144/http://www.caspa.com/austin/board_member.htm
CASPA Introduction (CASPA.com, 2008; archived: https://web.archive.org/web/20081020171639/http://www.caspa.com:80/about)
CASPA Sponsors (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202407/http://www.caspa.com/sponsors/diamond)
CASPA Platinum Sponsors (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202414/http://www.caspa.com/sponsors/platinum
CASPA Gold Sponsors (CASPA.com, 2008; archived: https://web.archive.org/web/20111026110417/http://www.caspa.com/sponsors/gold?page=1
CASPA Silver Sponsors (CASPA.com, 2008; archived: https://web.archive.org/web/20090831133050/http://www.caspa.com/sponsors/silver?page=1)
CASPA Austin Chapter (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202127/http://www.caspa.com:80/about/austin)
CASPA Dallas Chapter (CASPA.com, 2008, archived: https://web.archive.org/web/20081020202129/http://www.caspa.com:80/about/dallas)
CASPA Pearl River Delta Chapter (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202141/http://www.caspa.com:80/about/pearl)
CASPA Shanghai Chapter (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202150/http://www.caspa.com:80/about/shanghai)
CASPA Silicon Valley Chapter (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202155/http://www.caspa.com:80/about/silicon)
CASPA Phoenix Chapter (CASPA.com, 2008; archived: https://web.archive.org/web/20081020202145/http://www.caspa.com:80/about/phoenix)
CASPA Members (CASPA.com, 2019; archived: https://web.archive.org/web/20190528095828/http://www.caspa.com/members)
CASPA Diamond Sponsors (CASPA.com, 2022; archived: https://web.archive.org/web/20220617040441/https://caspa.com/diamond-sponsors/)
CASPA Platinum Sponsors (CASPA.com, 2022; archived: https://web.archive.org/web/20220124223758/https://caspa.com/platinum-sponsors/)
Danny Hua, LinkedIn (LinkedIn: https://www.linkedin.com/in/danny-hua-85186ab/details/experience/)
CASPA Diamond Sponsors (CASPA.com, 2024; archived: https://web.archive.org/web/20240906182739/https://caspa.com/diamond-sponsors/)
100th Anniversary Celebration (CIE, 2017; archived: https://conference.cie-sf.org/attachments/article/12/CIE%202017%20Proceeding_web.pdf)
CHINESE INSTITUTE OF ENGINEERS/USA 2008 (CHINESE INSTITUTE OF ENGINEERS, 2008; archived: https://web.archive.org/web/20150131061302/http://www.cieusa-gnyc.org:80/newsletter/CIE%20yearbook2008.pdf)
C100 Mourns the Loss of Y.C.. Yang (Committee of 100, 2016: https://www.committee100.org/media-center/c100-mourns-the-loss-of-y-c-yang/)
CIE-USA, In Recognition of CIE Life Members (CIEUSA-GNYC.org, 2018, 71; archived: https://web.archive.org/web/20191222005254/http://www.cieusa-gnyc.org:80/convention2018/2_CIE_2018_Convention_Journal_Proceeding_wAd_v4.pdf, 73)
H. Jonathan Chao, Co-authors (archived: https://web.archive.org/web/20250405061014/https://ieeexplore.ieee.org/author/37363151400/co-author)
Minghao Ye, LinkedIn (LinkedIn: https://www.linkedin.com/in/minghao-ye-403758166/)
Minghao Ye, Junjie Zhang, Zehua Guo, H. Jonathan Chao, Federated Traffic Engineering with Supervised Learning in Multi-region Networks (IEEE, 2021: https://icnp21.cs.ucr.edu/papers/icnp21camera-paper10.pdf)
Kangyao Huang personal website (archived: https://web.archive.org/web/20250404171420/https://kangyao-huang.tech/)
Xiaoyu Wang, Kangyao Huang, Xinyu Zhang, Honglin Sun, Wenzhuo Liu, Huaping Liu, Jun Li, Pingping Lu, Path Planning for Air-Ground Robot Considering Modal Switching Point Optimization (arXiv:2305.08178v1 [cs.RO] 14 May 2023; archived: https://web.archive.org/web/20240708055743/https://arxiv.org/pdf/2305.08178)
CIE-USA, In Recognition of CIE Life Members (CIEUSA-GNYC.org, 2018, 68; archived: https://web.archive.org/web/20191222005254/http://www.cieusa-gnyc.org:80/convention2018/2_CIE_2018_Convention_Journal_Proceeding_wAd_v4.pdf, 70)
ABOUT AAEOY (CIE-USA.net, archived: https://web.archive.org/web/20250405032856/https://cie-usa.net/?page_id=224)
Chinese Academy of Sciences Elects Subra Suresh as Foreign Member (Carnegie Mellon University, 29 August 2016; archived: https://web.archive.org/web/20250403060931/https://www.cmu.edu/engineering/materials/news_and_events/news/archive/2014/january/chinese-academy-of-sciences-elects-subra-suresh-as-foreign-member.html
Related Resources (US-CERT.govhttps://web.archive.org/web/20140314134521/https://www.us-cert.gov/related-resources)
U.S. Patent and Trademark Office Trademark Search (uspto.gov: https://tsdr.uspto.gov/#caseNumber=74725838&caseSearchType=US_APPLICATION&caseType=DEFAULT&searchType=statusSearch)
Elisabeth Paté Cornell, Stanford University (Stanford.edu, archived: https://web.archive.org/web/20220626162406/https://msande.stanford.edu/people/elisabeth-pate-cornell)
Former Harvard University Professor Sentenced for Lying About His Affiliation with Wuhan University of Technology; China’s Thousand Talents Program; and Filing False Tax Returns (U.S. Department of Justice, 26 April 2023; https://www.justice.gov/usao-ma/pr/former-harvard-university-professor-sentenced-lying-about-his-affiliation-wuhan)
阿尼尔·库马尔·贾恩(Anil Kumar Jain) (China Ministry of Science and Technology, archived: https://web.archive.org/web/20200421011054/http://casad.cas.cn/sourcedb_ad_cas/zw2/ysxx/wjysmd/201911/t20191121_4724722.html)
About Ming Hsieh, Titan of Technology (MHIcancer.usc.edu; archived: https://web.archive.org/web/20250406044104/https://mhicancer.usc.edu/ming-hsieh/)
复旦发展研究院全 (Fudan Institute of Development Studies, ; archived: https://web.archive.org/web/20240730101041/https://alumni.fudan.edu.cn/_upload/article/files/5a/1f/bc8b3de14d30b86818d2ab8e1690/6bf97fd8-2afb-412c-9d00-f6d50e3c4659.pdf)
Geninna Ariton, “SF Express founder Wang Wei is China’s 10th richest billionaire, but before that he was an illegal cross-border delivery man – here’s how he made his fortune” (South China Morning Post, 22 September 2020; archived: https://web.archive.org/web/20200922022423/https://www.scmp.com/magazines/style/news-trends/article/3102409/sf-express-founder-wang-wei-chinas-10th-richest)
诚意与服务:校友志愿劝募人 (“Fudan Tribe”, 44; archived: https://web.archive.org/web/20220303055854/https://alumni.fudan.edu.cn/_upload/article/files/9f/f8/6ad84b8049beb607c6a2a22ec0f5/4a84c476-eb5e-47b2-a129-1ff4af0f9faf.pdf, 46)
复旦发展研究院全 (Fudan Institute of Development Studies, 8; https://web.archive.org/web/20240730101041/https://alumni.fudan.edu.cn/_upload/article/files/5a/1f/bc8b3de14d30b86818d2ab8e1690/6bf97fd8-2afb-412c-9d00-f6d50e3c4659.pdf, 6)
Program Overview (fudan-uc.ucsd.edu, current: https://fudan-uc.ucsd.edu/about/index.html)
Fudan IMBA (Collaborate with MIT Sloan) (Fudan University, archived: https://web.archive.org/web/20241014060823/https://www.fdsm.fudan.edu.cn/fdimba/fudan-mit_imba.html)
Voyager Supercomputer Enters Testbed Phase (UC San Diego Today, 18 May 2022; archived: https://web.archive.org/web/20250406231745/https://library.ucsd.edu/dc/object/bb96022739/_1.pdf)
U.S. House Select Committee on the CCP, CCP ON THE QUAD: How American Taxpayers and Universities Fund the CCP’s Advanced Military and Technological Research (September, 2024; https://selectcommitteeontheccp.house.gov/sites/evo-subsites/selectcommitteeontheccp.house.gov/files/evo-media-document/2024-09-24%20Research%20Security%20Report%20Final.pdf)
第十三批国家“千人计划”青年项目拟入选人员名单 (archived: https://web.archive.org/web/20190827060240/https://www.rencai.gov.cn/Uploads/file/20170103/20170103102223_94395.pdf, redirects to: https://web.archive.org/web/20220311053453/http://www.gzrcwork.com/)
Jinqing Peng (etl.lbl.gov, archived: https://web.archive.org/web/20210320095256/https://eta.lbl.gov/people/Jinqing-Peng)
Fortinet Teams Up with The Hong Kong Polytechnic University to Launch Cybersecurity Training Academy (Fortinet, 24 January 2017; archived: https://web.archive.org/web/20200919170050/https://www.fortinet.com/corporate/about-us/newsroom/press-releases/2017/FNSA-HongKongPolyU-launch)
Nathan Walker (“GusQuixote”), “Which Team is Which?” (Substack.com, 7 January 2025; https://gusquixote.substack.com/i/154255967/the-fudan-uc-center)
UC San Diego, Our People (UC San Diego Fudan-UC Center, https://web.archive.org/web/20180607165909/http://fudan-uc.ucsd.edu/people/index.html#Executive-Board-)
Wikipedia, Renmin University of China (Wikipedia: https://en.wikipedia.org/wiki/Renmin_University_of_China)
2019 China Forum (UCSD, https://china.ucsd.edu/_files/china-forum_2019-participants.pdf
ProPublica Nonprofit Explorer search, “Fudan University” (ProPublica, https://projects.propublica.org/nonprofits/search?q=fudan+university)
Li Yang, Nation's US studies widen their reach (China Daily, 20 February 2019; archived: https://web.archive.org/web/20250409201033/https://www.chinadaily.com.cn/global/2019-02/20/content_37438515.htm)
Thomas Lum, U.S. Assistance Programs in China (Congressional Research Service, 2 December 2014; archived: https://web.archive.org/web/20220120054453/https://sgp.fas.org/crs/row/RS22663.pdf)
Thomas Lum, U.S.-Funded Assistance Programs in China (Congressional Research Service, Wikileaks, 28 January 2008; https://wikileaks.org/wiki/CRS-RS22663)
Fudan University Institute of Higher Education, “About Us” (Fudan University, https://ihe.fudan.edu.cn/AboutUs/list.htm)
ProPublica Nonprofit Explorer search, “Tsinghua” (ProPublica, https://projects.propublica.org/nonprofits/search?q=tsinghua)
Tsinghua University- Carnegie Mellon University Joint Master's Program (Tsinghua University, https://goglobal.tsinghua.edu.cn/en/program/p5mKcs45myLa)
BRICS Economic Think-tank (Tsinghua University Newsletter, Issue 27-April 2015; archived: https://web.archive.org/web/20220708085653/https://www.tsinghua.edu.cn/__local/8/30/F8/7CA0FA253BA50097134526E67B1_A24CA86E_1A878D.pdf?e=.pdf)
Tsinghua, UW and Microsoft launch Global Innovation Exchange Institute (Tsinghua University Newsletter, Issue 28-October 2015 ; archived: https://web.archive.org/web/20220708050820/https://www.tsinghua.edu.cn/__local/9/A4/69/A67D65B4ECCDD01DB4C0F55AE32_C41EE0BB_210C6E.pdf)
University of Washington, About the Global
Innovation Exchange (https://gix.uw.edu/about)
Tsinghua SEM, “Tsinghua Global MBA Program,” 2023; archived: https://web.archive.org/web/20250111184609/https://gmba.sem.tsinghua.edu.cn/Brochure_gmba2023.pdf)
Fudan-MIT International MBA Program (archived: https://web.archive.org/web/20180206020757/https://www.fdsm.fudan.edu.cn/fdrs/imba/files/zhaosheng0619.pdf)
Fudan International MBA (Fudan University, https://www.fdsm.fudan.edu.cn/fdrs/mba/download/Fudan-MITIMBABrochure.pdf; archived: https://archive.is/FFkGK, https://web.archive.org/web/20250410100145/https://www.fdsm.fudan.edu.cn/fdrs/mba/download/Fudan-MITIMBABrochure.pdf)
School of Economics and Management, Tsinghua University (Tsinghua University, 2022-2023, pp. 12-13; archived: https://web.archive.org/web/20231113005203/https://www.sem.tsinghua.edu.cn/en/2022-2023yuanceyuanwangbanying.pdf, p. 8)
School of Economics and Management, Tsinghua University (Tsinghua University, 2023-2024, pp. 12-13; archived: https://web.archive.org/web/20240603211740/https://www.sem.tsinghua.edu.cn/en/2023-2024yuanceyuanwangbanyingupdated.pdf)
School of Economics and Management, Tsinghua University (Tsinghua University, 2024-2025, pp. 12-13; archived: https://web.archive.org/web/20250410075831/https://www.sem.tsinghua.edu.cn/en/2024-2025TsinghuaSEMbrochure.pdf)
清华大学经济管理学院顾问委员会 The Advisory Board of Tsinghua University School of Economics and Management (Tsinghua University, 18 October 2023; archived: https://web.archive.org/web/20240910201846/https://www.sem.tsinghua.edu.cn/en/Tsinghua_SEM_Advisory_Board_Members_List_20231030.pdf)
Tsinghua University School Of Economics And Management Na Alumni Association Form 990-EZ, 2015 (https://projects.propublica.org/nonprofits/organizations/821545631/201841359349202834/full)
CGCC Chairman Chen Xu attends the “Inauguration Ceremony of Tsinghua University’s School of Economics and Management North America Alumni Association Eastern US Chapter (CGCC USA, 19 April, 2015; https://www.cgccusa.org/en/cgcc_chairman_chen_xu_attends_the_inauguration_ceremony_of_tsinghua_universitys_school_of_ec/; archived: https://archive.is/pKrU5)
Edward Kovacs, “Fortinet Confirms New Zero-Day Exploitation” (SecurityWeek, 15 January 2025, archived: https://www.securityweek.com/fortinet-confirms-new-zero-day-exploitation/)
Scott Caveza, “CVE-2024-55591: Fortinet Authentication Bypass Zero-Day Vulnerability Exploited in the Wild” (Tenable, 14 January 2025; archived: https://web.archive.org/web/20250411042657/https://www.tenable.com/blog/cve-2024-55591-fortinet-authentication-bypass-zero-day-vulnerability-exploited-in-the-wild)
Reuters, Former Federal Reserve adviser arrested for passing trade secrets to China, Justice Department says (Reuters, 31 January 2025; https://www.reuters.com/world/us/former-federal-reserve-adviser-arrested-passing-trade-secrets-china-justice-2025-01-31/)
Two Arrested and 13 Charged in Three Separate Cases for Alleged Participation in Malign Schemes in the United States on Behalf of the Government of the People’s Republic of China (U.S. Department of Justice, 24 October 2022; https://www.justice.gov/archives/opa/pr/two-arrested-and-13-charged-three-separate-cases-alleged-participation-malign-schemes-united)
Chinese Nationals with Ties to the PRC Government and “APT27” Charged in a Computer Hacking Campaign for Profit, Targeting Numerous U.S. Companies, Institutions, and Municipalities (U.S. Department of Justice, 5 March 2025; https://www.justice.gov/usao-dc/pr/chinese-nationals-ties-prc-government-and-apt27-charged-computer-hacking-campaign-profit)
Chinese Government Intelligence Officer Sentenced to 20 Years in Prison for Espionage Crimes, Attempting to Steal Trade Secrets From Cincinnati Company (U.S. Department of Justice, 16 Novemeber 2022; https://www.justice.gov/archives/opa/pr/chinese-government-intelligence-officer-sentenced-20-years-prison-espionage-crimes-attempting)
Alex Wong (UCSD, archived: https://web.archive.org/web/20250325220932/https://china.ucsd.edu/policy/china-forum/participants/alex-wong.html)
Ni, Lionel; Mutka, Matt; Enbody, Richard; McKinley, Philip, CISE Research Instrumentation ($77,000) (Grantome.com; https://grantome.com/grant/NSF/EIA-9121641)
NYPD Recovers 5-foot drone in Brooklyn, Linked to Sustainable Energy Startup (WCHS-TV, https://wchstv.com/news/nation-world/nypd-recovers-5-foot-drone-in-brooklyn-linked-to-sustainable-energy-startup-brooklyn-naval-yard-massive-ufo-uap-federal-government-joe-biden-white-house-congress-president-elect-donald-trump-mar-a-lago-amogy)
MIT Startup Exchange, Amogy (https://web.archive.org/web/20250411050723/https://startupexchange.mit.edu/node/30534)
Pierluigi Paganini, “In-flight Wi-Fi can be an open door for hackers” (Security Affairs, 17 April 2015; archived: https://securityaffairs.com/36059/hacking/in-flight-hacking.html)
Pierluigi Paganini, Equation Group APT and TAO NSA: Two Hacking Arsenals Too Similar (InfoSec Institute, 9 March 2015; archived: https://web.archive.org/web/20250410173146/https://www.infosecinstitute.com/resources/threat-intelligence/equation-group-apt-tao-nsa-two-hacking-arsenals-similar/)
Reuters, Exclusive-China Acquired Recently Banned Nvidia Chips in Super Micro, Dell Servers, Tenders Show (Reuters, 22 April 2024: https://www.reuters.com/world/china/china-acquired-recently-banned-nvidia-chips-super-micro-dell-servers-tenders-2024-04-23/)
Jeff Stone, “Fortinet settles charges of selling intentionally mislabeled Chinese-made tech to U.S. military” (CyberScoop, 16 April 2019; archived: https://web.archive.org/web/20190416212916/http://cyberscoop.com/fortinet-legal-settlement-china-us-military/)
Britney Nguyen, Nvidia asked Supermicro and Dell how its advanced AI chips ended up in China (Quartz, 19 December 2024; archived: https://qz.com/nvidia-supermicro-dell-ai-chips-china-us-export-control-1851725577)







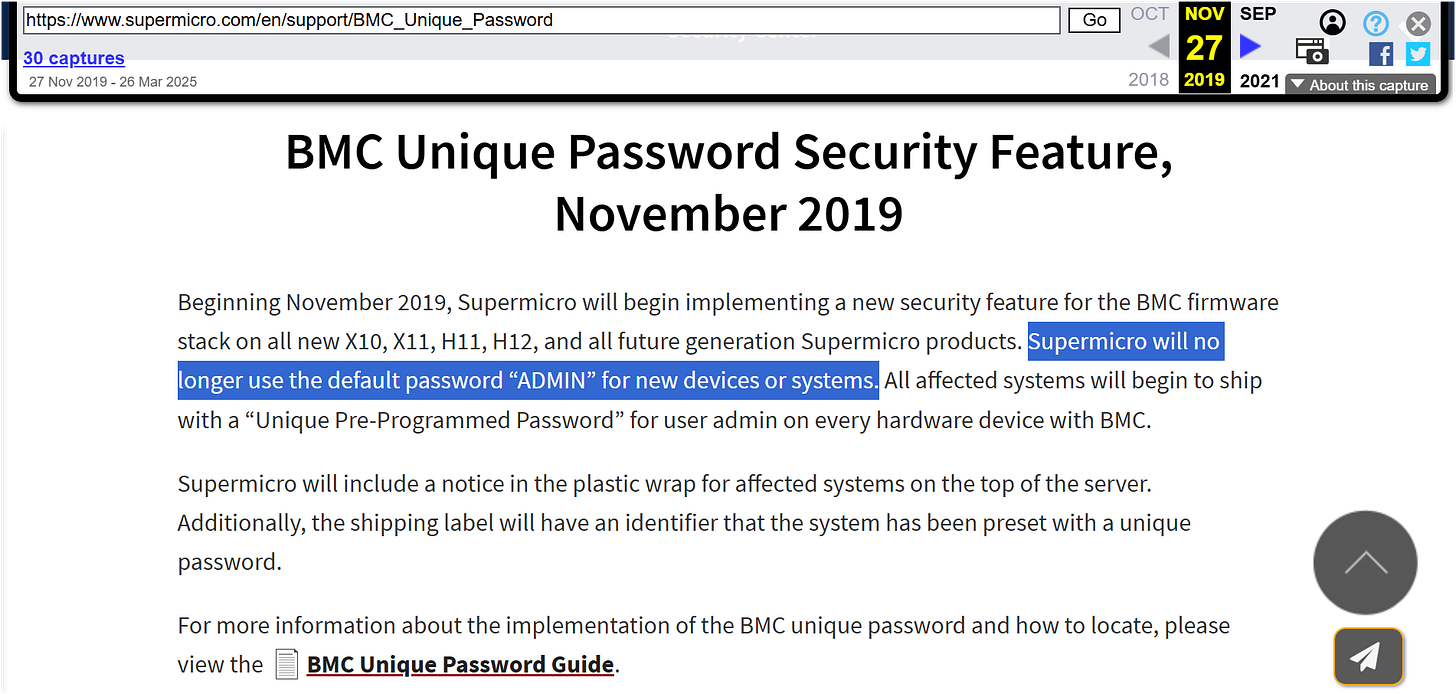
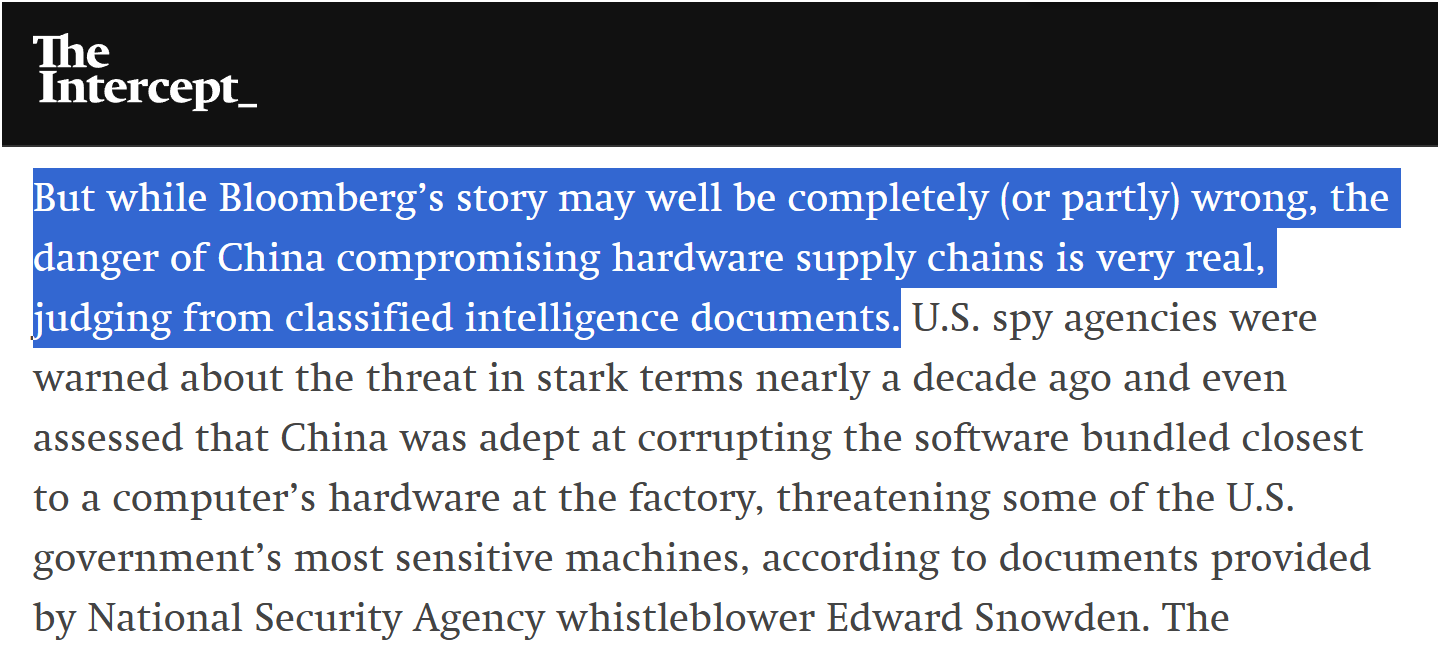
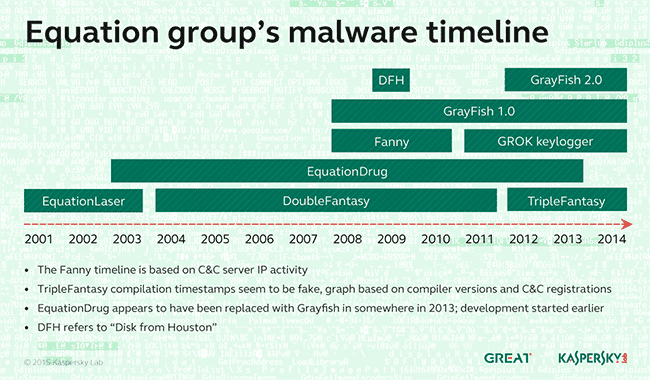





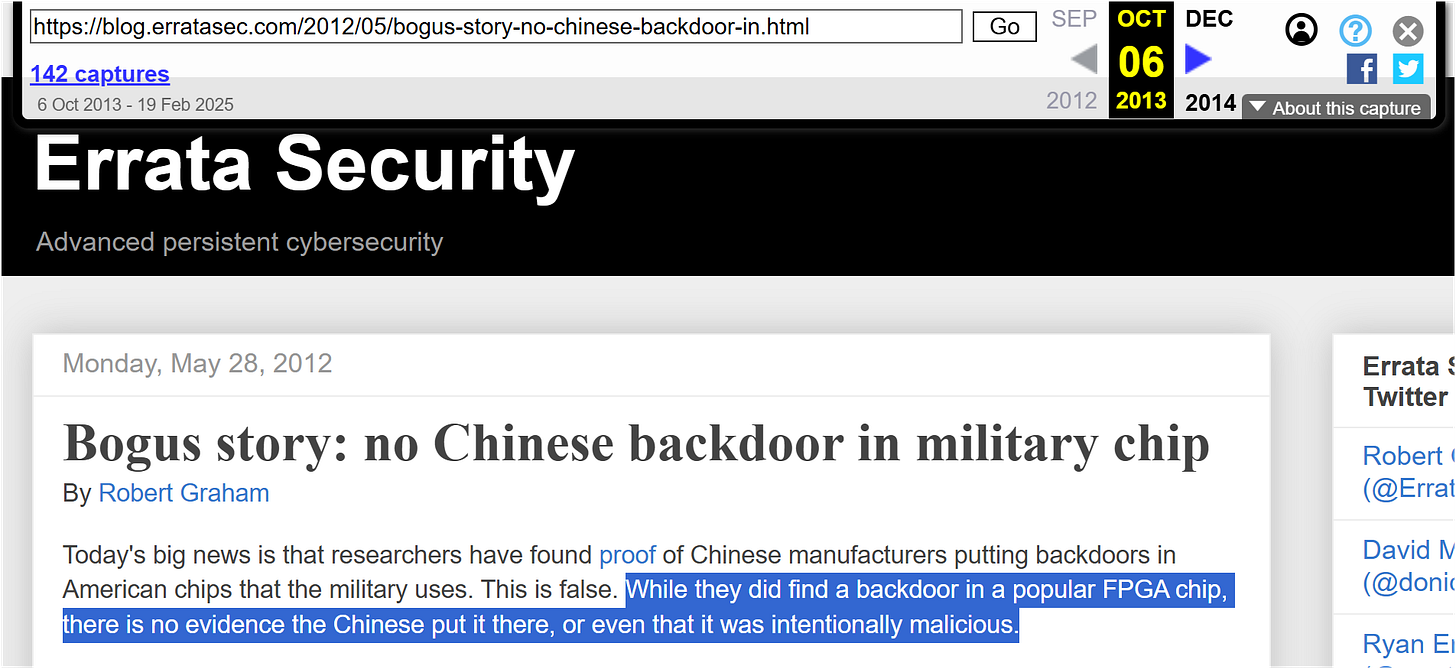









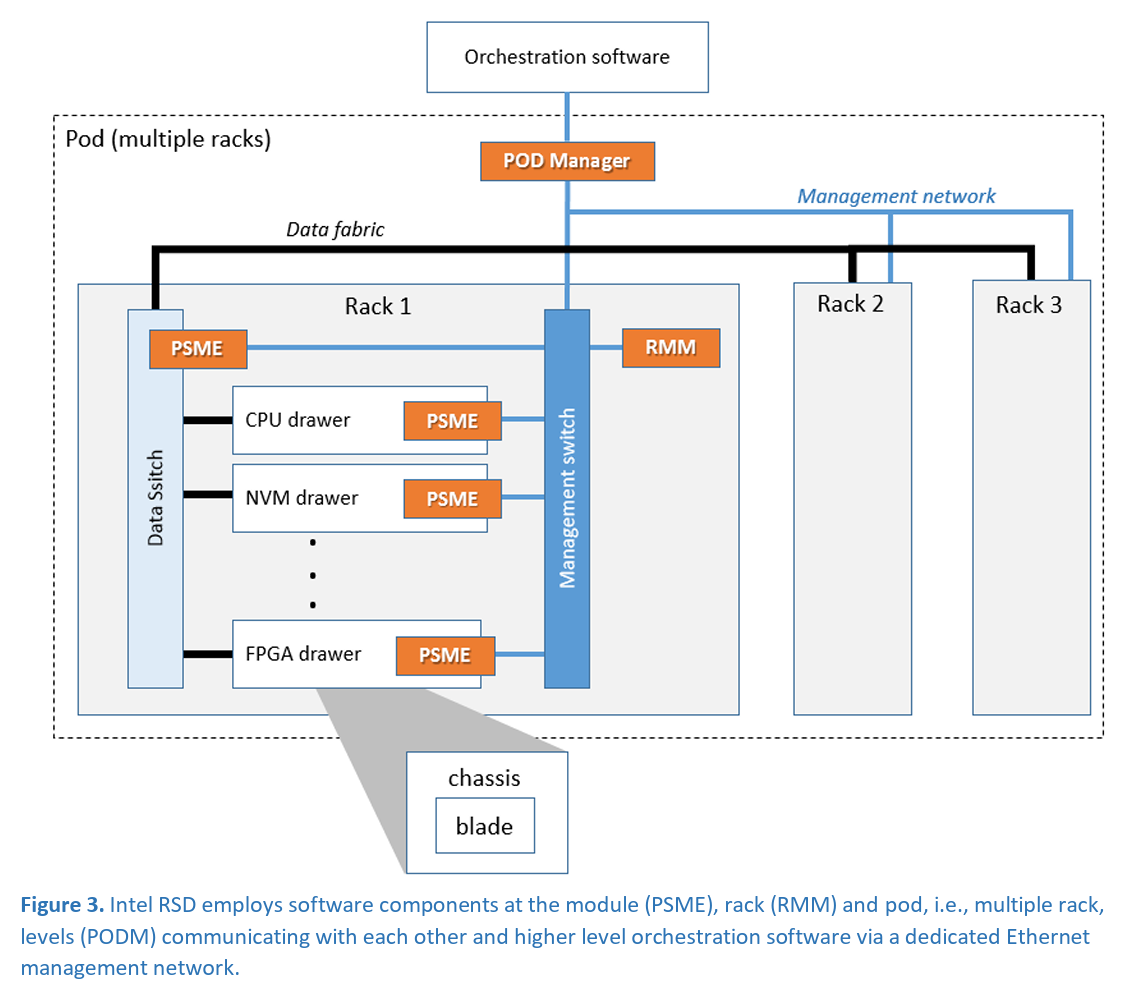














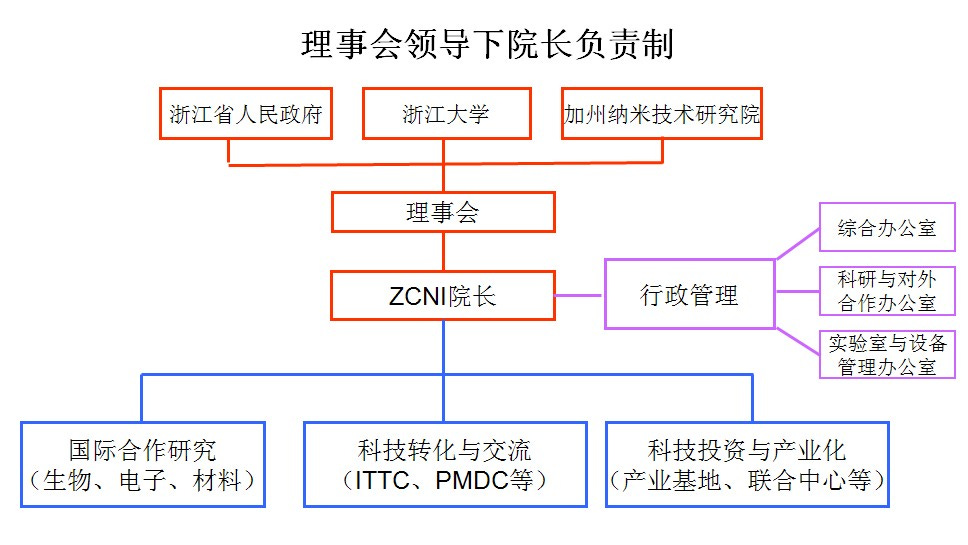


























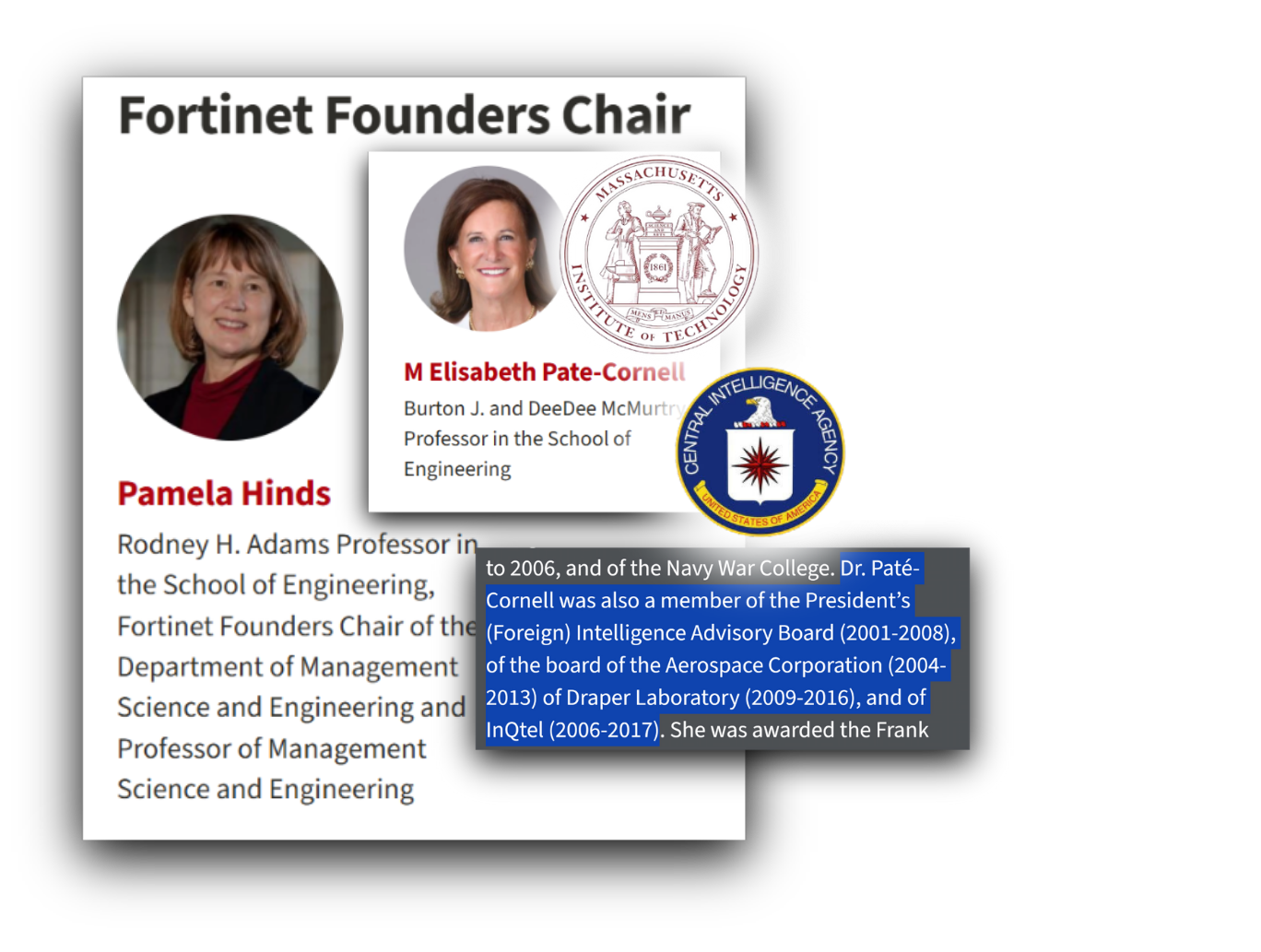


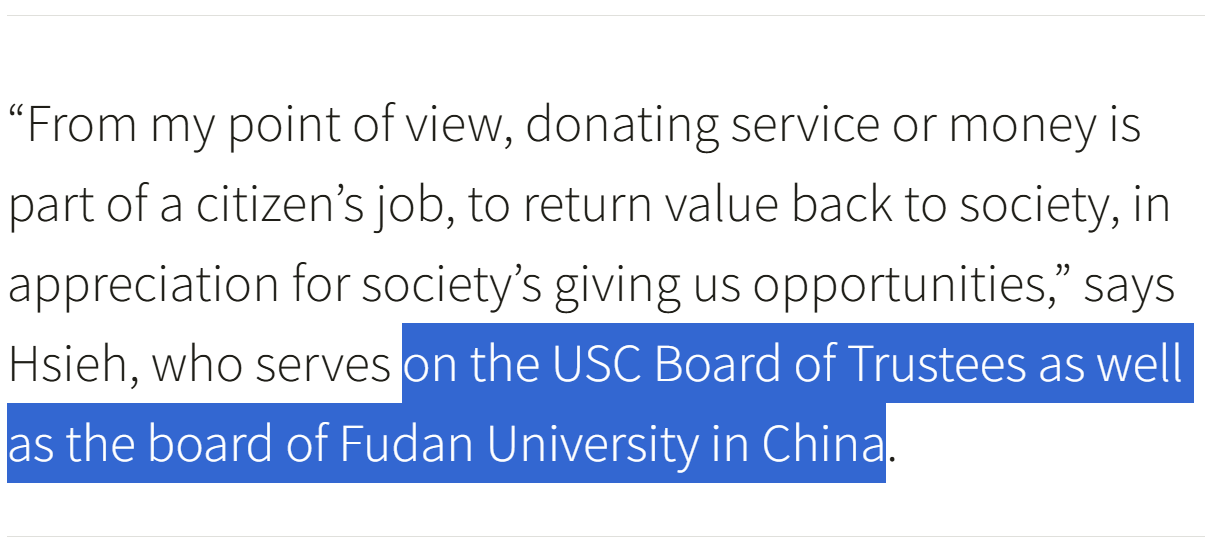
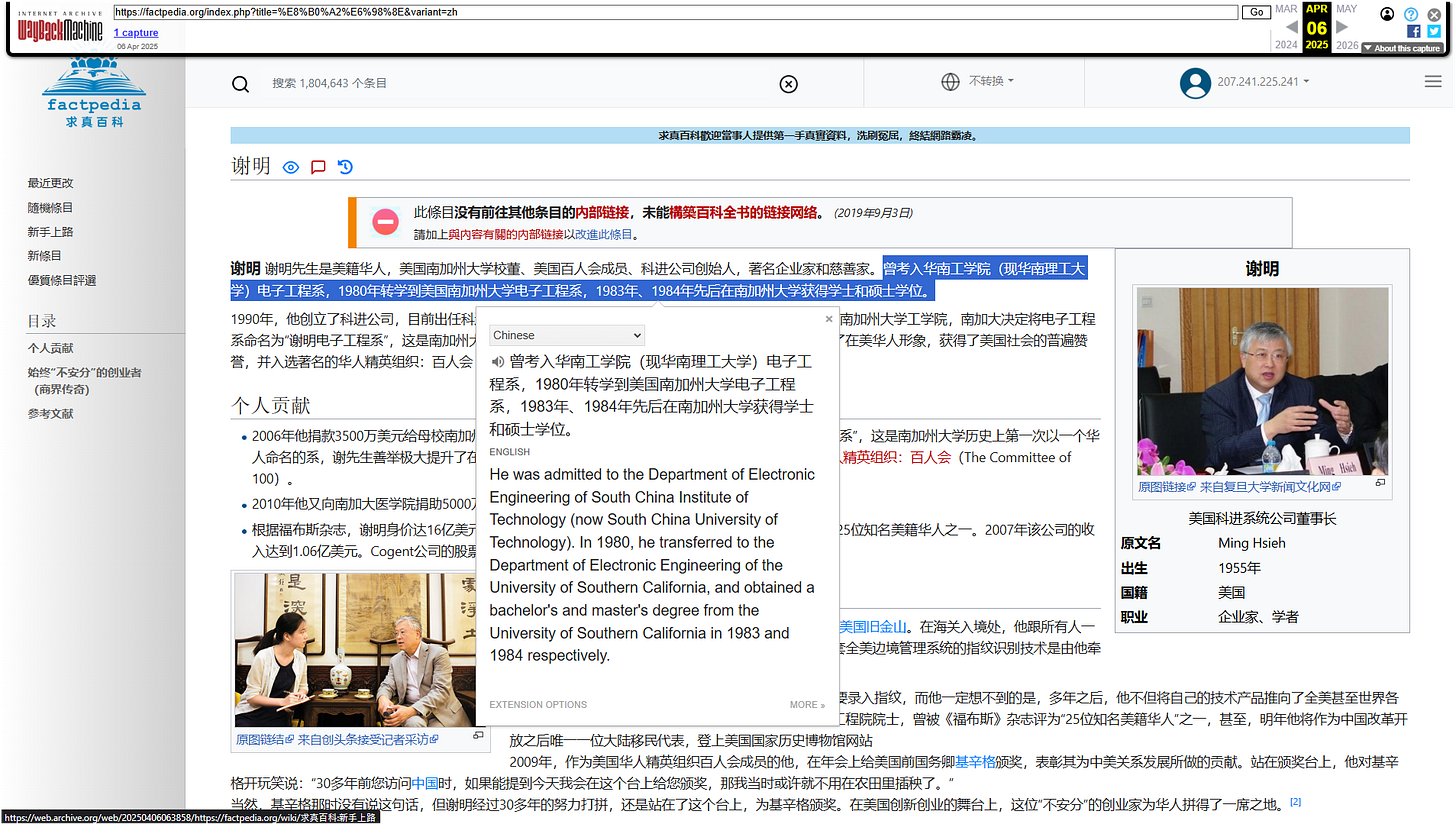
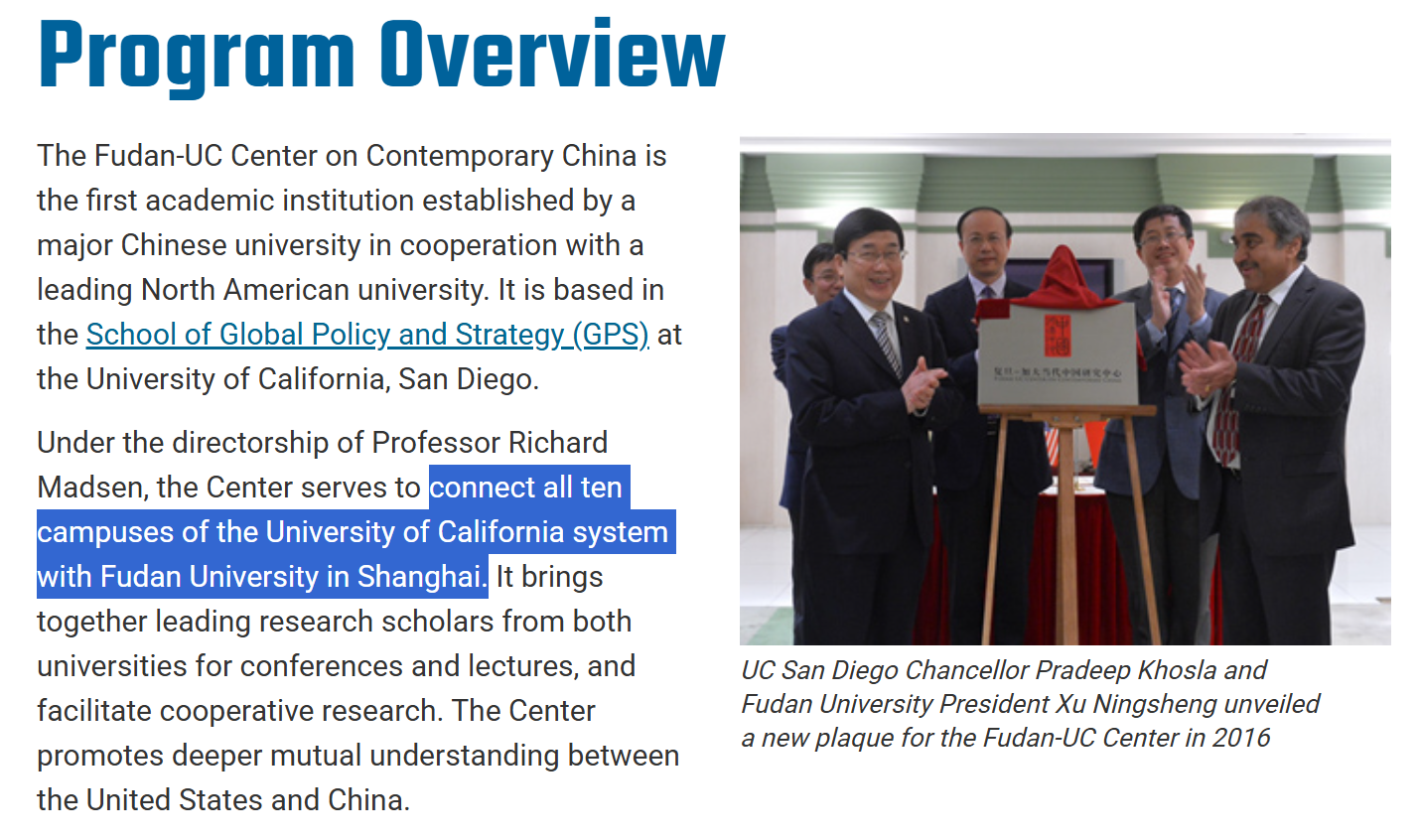








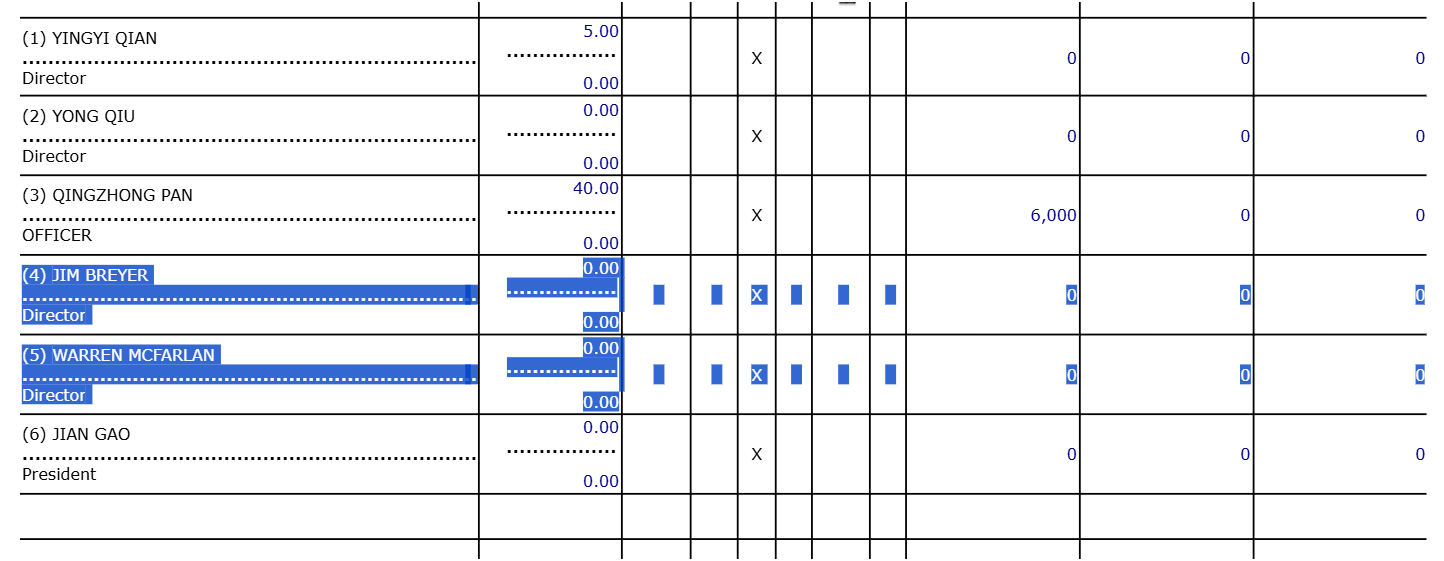











Wow great work putting all of this together - great article
Nice. Thanks for this.